Information Privateness is a subject that few wish to discuss when there isn’t any drawback in the mean time. Fortunately, the OWASP Prime 10 Privateness Dangers 2021 rating offers you a ready-made listing of privateness points in your app. To make it even higher, we summed it up for you within the type of an actionable information so it can save you much more time. Meet the threats, keep away from them, and stop your customers’ anger, PR disasters, lawsuits, and an enormous headache within the course of!
OWASP safety rankings akin to…
convey tons of useful up-to-date insights on how you can defend your software program from safety threats.

What’s the OWASP Prime 10 Privateness Dangers rating?
The OWASP Prime 10 Privateness Dangers 2021 is much less well-known than the rankings I discussed earlier than however simply as vital and helpful. The privateness points it lists embody each technological and organizational features of net functions. It focuses on actual threats relatively than simply authorized issues.
Naturally, it additionally gives recommendation on how you can forestall or overcome these threats based mostly on the OECD Privateness Pointers. As such, you should utilize it for knowledge privateness threat evaluation in net growth.
Prime 10 Privateness Dangers 2014
The unique rating hit the digital cabinets in 2014, however so many new instruments and strategies have proven up ever since. The Normal Information Safety Regulation act additionally performed an element in making the unique rating considerably out of date.
Only for a reminder, the threats had been as follows:
- Internet Utility Vulnerabilities
- Operator-sided Information Leakage
- Inadequate Information Breach Response
- Inadequate Deletion of Person Information
- Non-Clear Insurance policies, Phrases, and Circumstances
- Assortment of Information Not Required for the Person-Consented Goal
- Sharing of knowledge with third celebration
- Outdated private knowledge
- Lacking of Inadequate Session Expiration
- Insecure Information Switch
How did the listing change over all of these years? Let’s not waste any extra time and delve proper into it!
#1 Internet Utility Vulnerabilities
⏱️ Frequency: Excessive,
? Influence: Very excessive,
? Kind: Organizational
This privateness threat is a transparent shout-out to the OWASP Prime 10 net app vulnerabilities listing. It’s all about the way you design your net app and whether or not you’ll be able to reply instantly to any potential points which will lead to knowledge privateness breaches.
To be able to try this, it’s essential to:
- carry out penetration checks,
- do common vulnerability and privateness checkups with instruments akin to Static Utility Safety Testing (SAST), Interactive Utility Safety Testing (IAST), or Dynamic Utility Safety Testing (DAST),
- implement acceptable counter-measures,
- educate programmers and designers on net growth safety,
- introduce protected processes akin to Safety Improvement Lifecycle (SDL) and DevSecOps,
- patch up your app in accordance with the wants and trade greatest practices.
How do corporations implement it in apply?
TSH response
At The Software program Home, we do the next:
- For every consumer, we feature out a vulnerability evaluation process. With that, we will catch a whole lot of vulnerabilities earlier than the app is even launched.
- Along with that, we kind up a safety crew that consists of DevOps, QA, and safety specialists in addition to a CTO. It makes communication on evaluation and debugging simpler.
- Lastly, we developed company-wide requirements based mostly on our personal expertise from quite a few huge industrial initiatives. It included a listing of processes to be applied in case of discovering vulnerabilities and a pre-deploy safety guidelines. Shortened variations of each of those paperwork can be found to all crew members. The safety crew handles specialised data, audits, and consultations.
Let’s go to extra explicit vulnerabilities.

#2 Operator-sided Information Leakage
⏱️ Frequency: Excessive,
? Influence: Very excessive,
? Kind: Organizational / Technical
This one is all about stopping leakages of any consumer knowledge the lack of which might represent a breach of confidentiality. Generally it’s attributable to an precise cyber assault, however additionally it is usually the results of errors, together with botched entry management administration, improper knowledge storage, or knowledge duplication.
One of the best ways to stop all that is to be choosy about your knowledge operators. Earlier than you entrust them along with your knowledge, you may wish to:
- verify their historical past of knowledge breaches in addition to their knowledge privateness greatest practices,
- Discover out whether or not they take part in a bug bounty program (rewards customers for locating bugs),
- make it possible for their nation of origin upholds larger knowledge safety requirements,
- enquire about their data safety certificates akin to ISO/IEC 27001/2, ISO/IEC 27017/18, or ISO/IEC 27701,
- carry out an audit to search out out extra about how they deal with knowledge (i.e. if they’ve a devoted knowledge privateness crew, safety coaching, how they anonymize knowledge, deal with entry administration, encryption keys).
You also needs to bear in mind at any time about:
- knowledge authentication (together with multi-factor authentication), authorization, and entry administration,
- the precept of least privilege – solely give entry to what’s wanted for a consumer to carry out a job,
- privateness by design,
- utilizing sturdy encryption for your whole consumer knowledge (together with so-called knowledge at relaxation), particularly for transportable knowledge storage units,
- implementing greatest practices akin to correct coaching, monitoring, private knowledge anonymization or pseudo anonymization,
- introducing knowledge classification and data administration coverage.
How does it work in apply?
TSH response
At my firm, all of those greatest practices are woven into the event course of. We implement them by audits, vulnerability assessments, or consultations with the crew. Over time, we developed a transferable knowledge safety greatest practices set, however we additionally modified it to fulfill the precise wants of some explicit purchasers. Safety coaching can also be an enormous a part of our onboarding. Every new worker will get to find out about knowledge processing, multi-factor authentication, password managers akin to 1Password, phishing prevention measures, the significance of doing backups, and extra.
Aside from that, we use the providers of corporations that care about knowledge privateness and cling to GDPR, ISO, and so on. That features AWS for internet hosting and cloud computing, or Firebase for app growth.

#3 Inadequate Information Breach Response
⏱️ Frequency: Excessive,
? Influence: Very excessive,
? Kind: Organizational / Technical
Should you don’t inform the victims correctly about delicate knowledge publicity, you might have an inadequate knowledge breach response. Failing to behave on these safety dangers could not solely lead to dropping purchasers but in addition in very expensive lawsuits and monetary penalties. One Polish on-line retailer was made painfully conscious of this when Poland’s Private Information Safety Workplace (UODO) punished it with a positive of €645,000 for a knowledge breach that affected roughly round 2.2 million prospects.
Initially, you want a knowledge breach response plan. You additionally want to check it and replace it frequently. The plan must be backed by a crew and incident monitoring software program (Safety Data and Occasion Administration or SIEM). For every occasion that came about prior to now, it’s essential to confirm if the response was enough, well timed, exact, and straightforward to know for all of the related events.
TSH response
As per our suggestions, a great knowledge department response crew or Laptop Emergency Response Crew (CERT) is the important thing. Then, it’s all about monitoring. As soon as a breach happens, the response crew assembles to confirm the vulnerability and resolve if and the way somebody ought to be knowledgeable about it. Every incident is assigned a precedence and the response is carried out accordingly.
We now have our personal procedures for all of those actions, however we additionally align them with the most effective practices of our purchasers.
#4 Consent on The whole lot
⏱️ Frequency: Very Excessive,
? Influence: Very excessive,
? Kind: Organizational
A misuse of consent for the processing of private knowledge is getting more and more frequent.
Oftentimes, corporations ask for content material for “every little thing”, relatively than for each aim individually (e.g. utilizing the web site and profiling for advert functions are two totally different areas). It’s essential to have seen these cookie pop-ups that inform you one thing about utilizing cookies and just about nothing else. The consumer ought to be capable of consent and withdraw consent for numerous actions. They need to albo be capable of take away pointless knowledge.
TSH response
To be able to forestall this, it’s essential to:
- verify if the consents are aggregated and processed correctly,
- verify if consents for non-essential actions and knowledge are switched off by default,
- acquire consents for every aim individually.
#5 Non-Clear Insurance policies, Phrases, and Circumstances
⏱️ Frequency: Very Excessive,
? Influence: Excessive,
? Kind: Organizational
This one is clearly associated to the earlier one. It’s about unclear data on how consumer knowledge is gathered, saved, and processed.
It is a very attention-grabbing drawback with some very stunning and eye-opening viewpoints. For instance, in an attention-grabbing article titled “Cease Considering About Consent: It isn’t potential and it isn’t proper”, digital privateness thinker Helen Nissenbaum argues that organizations will not be in a position to produce a totally clear consent discover as a result of, within the dynamic world of latest applied sciences, they merely can’t set up with certainty how precisely the gathered knowledge will probably be used. What’s extra, consenting to knowledge processing is commonly needed to make use of a given web site. She believes that within the subject of privateness, there’s something referred to as “an acceptable circulation of data”. In different phrases, we must always restrict privateness necessities by default to the extent it’s wanted to facilitate communication between two events.
What are some issues you are able to do?
From the service supplier’s standpoint, it’s best to positively confirm in case your phrases of use, insurance policies and different paperwork are simple to search out and perceive. The Hold It Quick and Candy or KISS precept is beneficial right here – it shouldn’t be any longer than it must be.
Along with that:
- the language ought to be clear and the info processing paperwork ought to embody data on knowledge retention time, metadata, consumer rights in addition to the place and when the info is processed,
- graphics could make it simpler for customers to know the content material,
- a great apply is to listing all of the cookies and what they do,
- relationship coverage updates may make it simpler for customers to remain within the loop,
- you also needs to maintain monitor of which customers consent to which coverage variations, informing these customers about new updates,
- and an opt-out button for all of the cookies ought to be available and clearly seen.
Do we’ve some strategies of our personal for that?
TSH response – the readability rating
Aside from these normal enhancements, you can even use a readability rating tester to search out out in case your textual content content material is simple to observe. I made the take a look at in three alternative ways:
- by pasting a URL instantly,
- by exporting the textual content to a file,
- by copying a chunk of textual content.
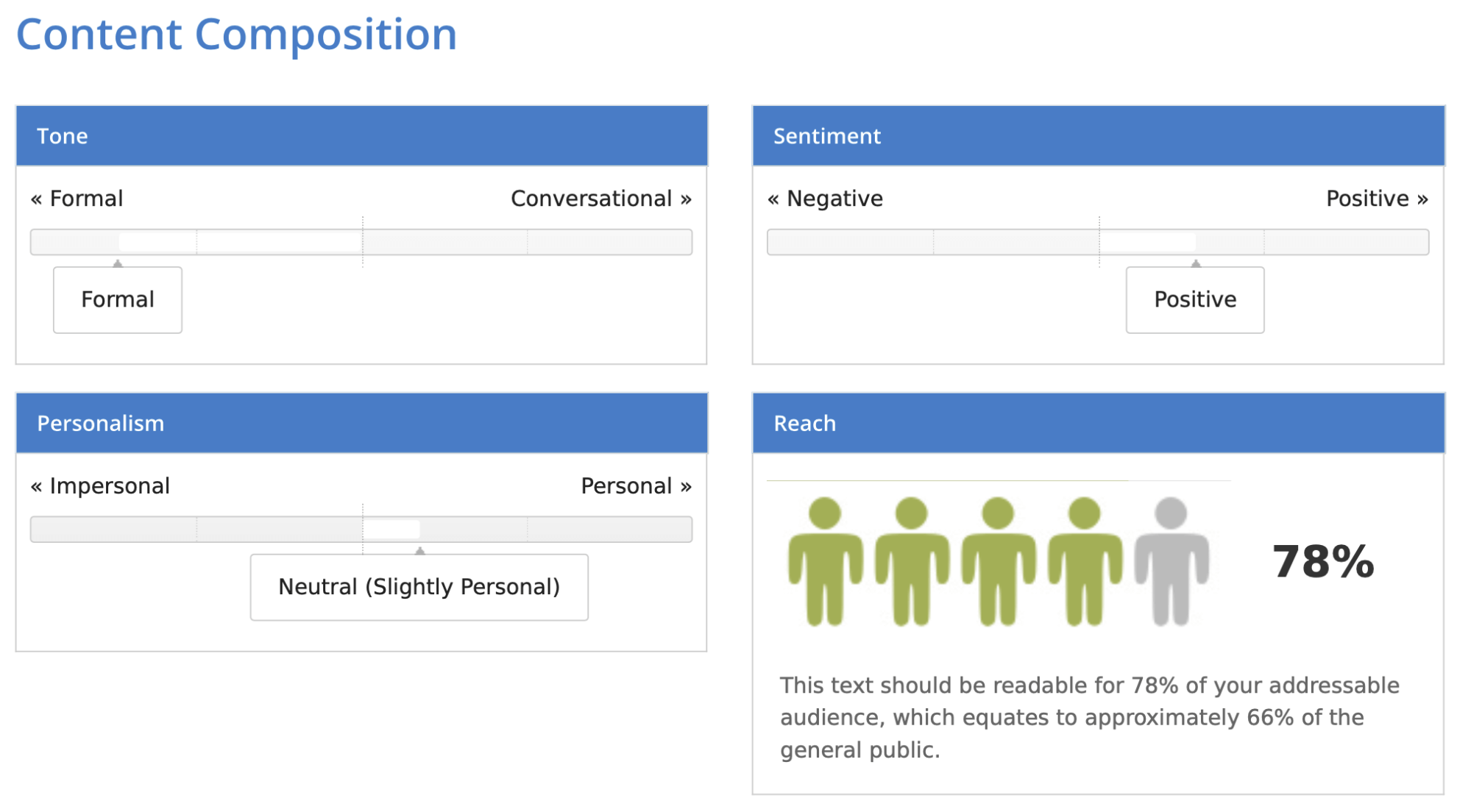
Curiously, the outcomes barely differ relying on the tactic. The direct methodology received the bottom rating of 78%.
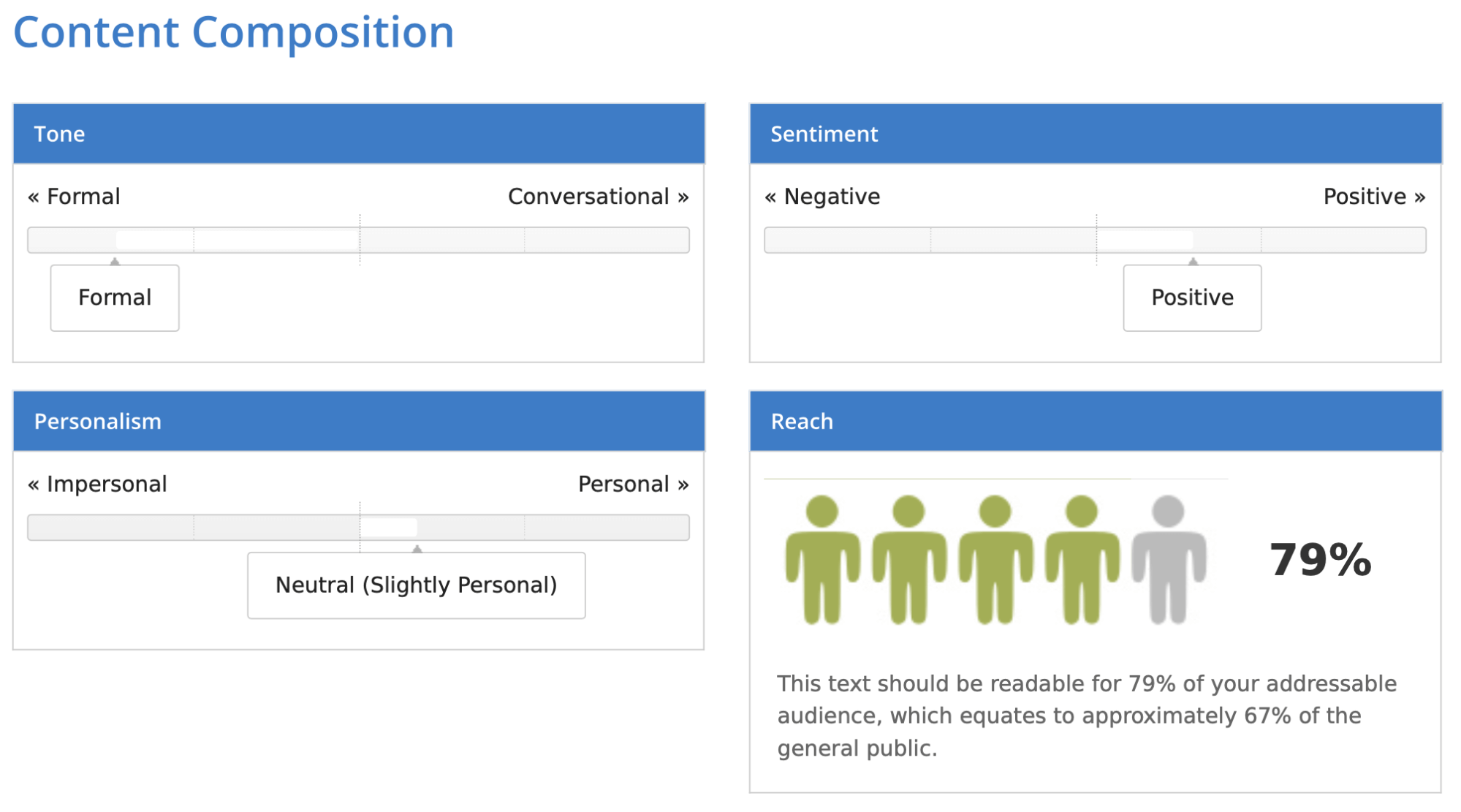
Then, I exported the entire coverage and uploaded the file into this system. This time, I received 79 %.
Lastly, the copied and pasted model acquired 82%.
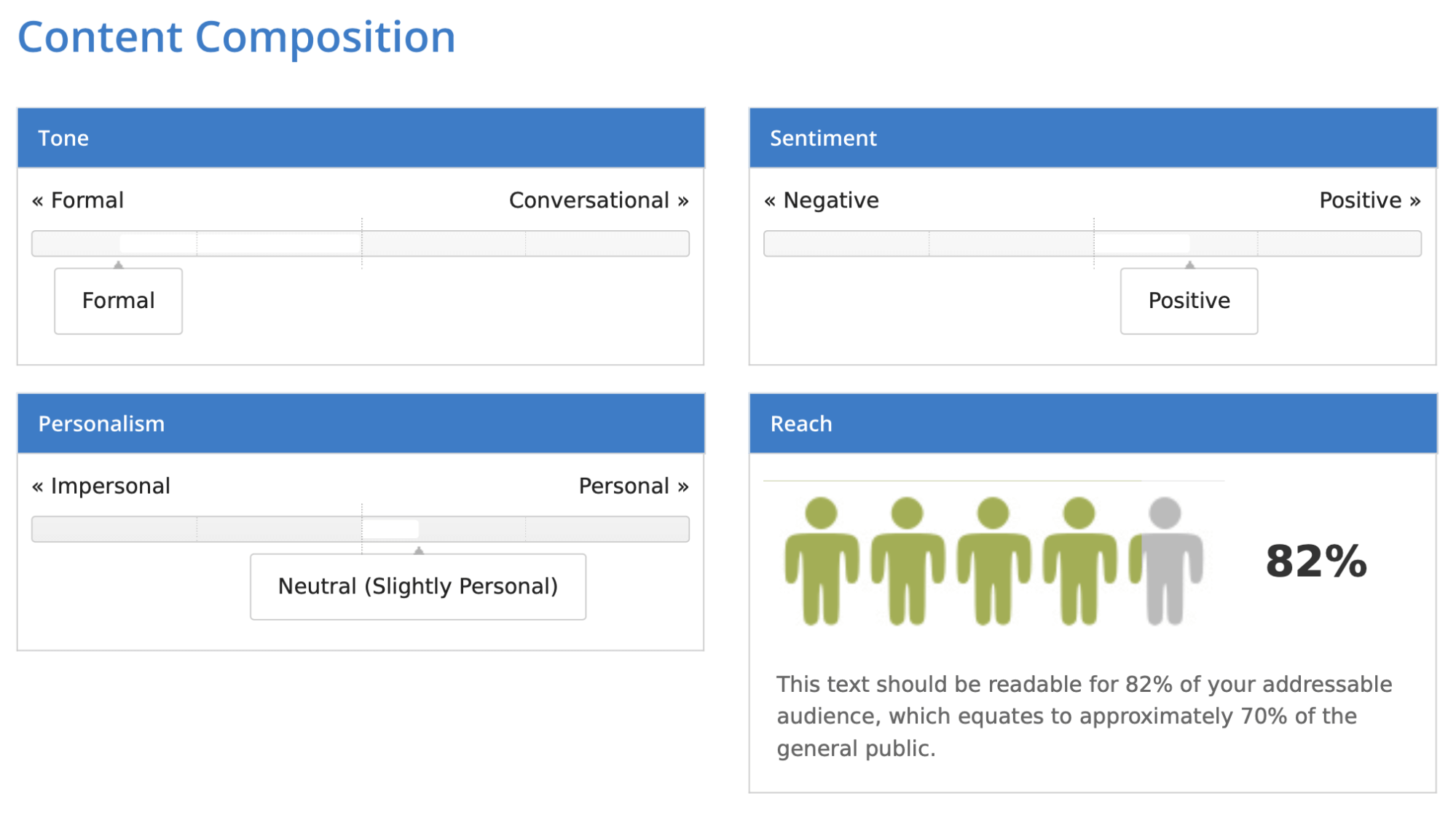
Evidently the device isn’t ultimate, but it surely does present a normal understanding of how readable your textual content is. You can even be taught extra about its tone. The one I uploaded turned out to be fairly formal, considerably constructive, and barely private. You also needs to account for correct names – these had been in Polish and so they had been marked purple as spelling errors because the device makes use of English.
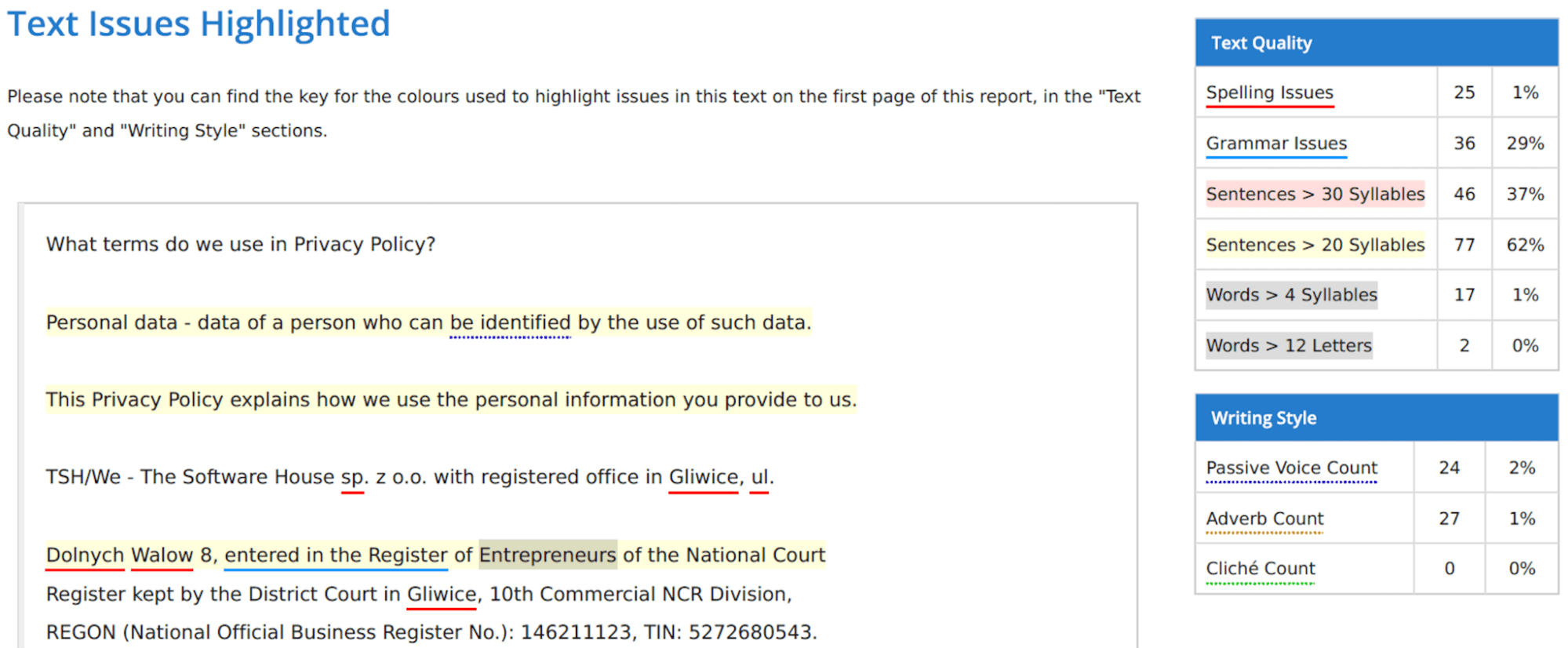
Given these situations, the 78-82% rating isn’t too dangerous. It signifies that round 66-70% of persons are in a position to learn the textual content.
If you need extra, it’s best to be taught extra in regards to the a11y accessibility testing course of from my pals at TSH!
- An ideal course of for a11y accessibility testing – in accordance with TSH’s QA engineering queens
#6 Inadequate Deletion of Person Information
⏱️ Frequency: Excessive,
? Influence: Excessive,
? Kind: Organizational / Technical
As soon as the info processing function is achieved, private knowledge ought to be eliminated. Sadly, it isn’t all the time the case. Organizations lack knowledge retention/elimination insurance policies. This usually results in numerous breaches of privateness.
To be able to amend it, it’s best to:
- embody this side in your knowledge privateness coverage, monitor knowledge and doc what occurs to it,
- decide when knowledge is eliminated as soon as it helped you obtain your acknowledged aim,
- implement safe wanting (extraordinarily restricted entry to knowledge) when eradicating such knowledge is unimaginable,
- take into account deleting consumer accounts when they’re unused over a time frame or not wanted,
- acquire proof so to confirm if knowledge was eliminated in accordance along with your coverage,
- take into account degaussing for cloud, that’s the cryptographic wiping of archived and backed-up knowledge.
How does it take a look at The Software program Home?
TSH response
In every of our initiatives, we attempt to maintain the consumer updated about our personal worker retention. JIRA or Slack accounts of those that depart are swiftly deactivated. We strictly observe a notion that an individual who left the corporate should not have any entry to any communication channels, environments (even testing ones!), or repos of the consumer.
On the worker’s half, they’re instructed to sign off of all of the providers and apps on their firm’s laptops and take away all of the content material, customization, and configuration. As soon as that is achieved, they’re to put in the newest model of the system.
On the day the worker fingers over the laptop computer, the worker’s entry settings in addition to e mail accounts are deleted. If an worker returns to our firm later, we make new accounts and supply them with all the required accesses from scratch. That approach, we guarantee the protection of each our personal and the consumer’s knowledge.
Need to be taught extra about how we purchase and retain builders? Try this acquisition and retention article from our CEO!
- The way to rent builders & maintain them for longer: A information by The Software program Home
#7 Inadequate Information High quality
⏱️ Frequency: Medium,
? Influence: Very excessive,
? Kind: Organizational / Technical
Generally, a company makes use of outdated, incorrect, or flat-out false consumer knowledge. How is that potential?
Imprecise kinds, technical errors (throughout logging or saving), or flawed knowledge aggregation (e.g. associated to cookies or social community account integration) could also be guilty. Sadly, the choice to edit or take away knowledge could also be very restricted in some functions. I personally skilled that when logging in to my Shopee account with a Fb account – after I wished to vary my fee card particulars, the app requested for a password, which I didn’t have as a consequence of registering with a third-party account.
Testing this explicit vulnerability is kind of simple. It is advisable ask the info operator if:
- the non-public knowledge they’ve is up-to-date,
- they management the info’s accuracy by asking the consumer about it frequently,
- you possibly can edit the info at your comfort.
In brief, it’s essential to implement knowledge validation processes (together with frequent copy & paste errors) to stop amassing and producing untrusted knowledge, be sure that to replace it (with third events aware about the info too!), and confirm the info with the consumer after they carry out vital actions.
TSH response
We be sure that to keep away from this vulnerability by storing up-to-date knowledge in safe apps. The worker can change it at any time.
From a regulation’s perspective, a serious change akin to updating your title or place of residence solely requires sending one assertion to the HR division. There isn’t any want for updating the worker contract or making an annex to it. Solely the following contract we signal sooner or later will replicate the brand new modifications. And after they do signal it, they now may use a protected and handy one-click e-signature supplied by suppliers akin to Autenti.
Along with that, we additionally ask every worker to confirm their place of residence every time we ship them paperwork or gear.
#8 Lacking or Inadequate Session Expiration
⏱️ Frequency: Medium,
? Influence: Very excessive,
? Kind: Technical
Should you don’t take enough session expiration measures, your customers could find yourself supplying you with greater than you want with out even realizing. Typical causes for this vulnerability embody not setting a session period restrict or hiding the logout button.
If the session continues to be lively and another person will get entry to the gadget, they could even nonetheless or manipulate the unique consumer’s knowledge.
The best approach to forestall that is to implement the computerized session expiration mechanism. Its period could differ relying on the kind of software or the significance of the info. You may also set a session period restrict (not than every week and as brief as 10 minutes for a lot of banking apps). You may take into account letting your customers set the numbers themselves.
TSH response
All of those greatest practices talked about above are additionally a normal in our initiatives. The Software program Home’s QA crew all the time makes positive to check these easy session-related measures. The safety crew double-checks it throughout its personal audits.
#9 Lack of ability of Customers to Entry and Modify Information
⏱️ Frequency: Excessive,
? Influence: Excessive,
? Kind: Organizational / Technical
When the consumer can’t entry or modify their knowledge, together with knowledge saved by third-party suppliers, with their very own consumer enter, you’ve received yet one more vulnerability – damaged entry management.
You may make the info out there for modification primarily by:
- a consumer account,
- a particular kind,
- or an e mail.
It’s very important that you simply make it possible for knowledge modification requests are resolved shortly.
TSH response
On our finish, this explicit subject has already been lined nicely above within the vulnerability regarding inadequate knowledge high quality. Aside from that, we observe the exact same greatest practices talked about on this part.
#10 Assortment of Information Not Required for the Person-Consented Goal
⏱️ Frequency: Excessive,
? Influence: Excessive,
? Kind: Organizational
Every bit of knowledge you ask for could pose some form of privateness threat. Due to that, it’s extremely really useful that you simply don’t acquire any knowledge that you simply don’t completely require. If knowledge is split into main and secondary when it comes to significance, it’s essential to make it clear to the top consumer. You additionally have to replace the data for those who change the precedence classification of a given piece of knowledge.
A very good instance of that vulnerability is an e-commerce platform that gives customized advertisements by default, with no regard for consumer consent. As a substitute, the consumer ought to first opt-in to obtain such content material. Equally, when a web site collects emails with a purpose to verify orders, it ought to explicitly ask if it additionally desires to make use of the e-mail in its e-newsletter campaigns.
TSH response
At The Software program Home, we all the time create clear definitions for every of the info processing targets, nicely earlier than any precise knowledge assortment begins. We suggest taking as little consumer knowledge by default as potential. If the consumer desires to gather extra, it ought to ask the consumer for permission explicitly.
Conclusions – put together your self for OWASP Prime 10 Privateness Dangers
The most recent vulnerability listing from OWASP exhibits simply what number of privateness threats anticipate each app creators and customers.
To be able to defend your online business, not solely do you want correct measures on the growth stage, but in addition on the organizational stage.
We lined the previous intimately above. As for the latter, The Software program Home continues to enhance in numerous methods, particularly by:
- implementing trade requirements akin to GDRP or ISO,
- writing good privateness insurance policies,
- organizing and creating a devoted safety crew,
- conducting safety audits and vulnerability checks to search out issues and lift normal consciousness of those points,
- educating our workers by onboarding, displays, or a e-newsletter,
- preserving the QA crew updated with all of the newest safety tendencies (relating to each net apps and APIs),
- creating a greatest practices guidelines (based mostly on ASVS – OWASP’s very personal Utility Safety Verification Customary) designed so that every worker can management app safety on their very own.
Not solely do all of those measures decrease OWASP Privateness Dangers, but in addition enhance the general high quality of our software program merchandise.
We suggest you do the identical.
And if you seek for a software program supplier to assist develop your subsequent software…
… decide one which has already made the trouble. In any case, the safety of your purchasers is at stake.

















![The Most Visited Websites in the World [Infographic]](https://newselfnewlife.com/wp-content/uploads/2025/05/Z3M6Ly9kaXZlc2l0ZS1zdG9yYWdlL2RpdmVpbWFnZS9tb3N0X3Zpc2l0ZWRfd2Vic2l0ZXMyLnBuZw.webp-120x86.webp)







