Cybersecurity isn’t solely about guaranteeing the safety of internet functions, but additionally offering it to cell functions or API. Why API? So as to make the styling, UX, and efficiency excellent, you’ll be able to’t neglect about API – the appliance that can talk with our backend. The security of the backend is essential to your app’s security, operate, and your customers’ delicate information. The attacker is not going to solely deal with purchasers (internet app, cell app, sensors, and so forth.) however will look deeper into the vulnerability.
A extremely popular SQL injection vulnerability is strictly associated to information manipulation in a database. It’s a preventable vulnerability.
An instance is the damaged API Authorization vulnerability that was present in a pleasant manner by Omkar Bhagwat (th3_hidd3n_mist). This vulnerability made it doable to delete, take over or study the delicate information of 1000’s of subdomains with out interacting with the consumer.
Now that you recognize you need this and want this in your undertaking, let’s check out API safety assessments (an software that’s used to speak with different functions/units on the backend). It’s value noting that the OWASP (Open Internet Utility Safety Undertaking) group 2019 ready a rating of the ten most typical API vulnerabilities, known as API Safety High 10 2019.
The undertaking updates information each few years, and so will we – as soon as OWASP publishes once more, most likely someday in 2023.
API safety and sorts of initiatives
Making certain API safety is necessary as a result of it could not solely apply to 1 system, nevertheless it has the flexibility to hook up with a number of, e.g. sensors, phone, internet functions, automobiles, and TV.
A ton of vulnerabilities are straightforward to test for – guaranteeing they’re coated ought to at all times be in your undertaking plan. I’m a fan of the OWASP group, and I primarily based my examples of preventing with vulnerabilities on their analysis.
API Safety High 10, much like the OWASP High 10 report for internet functions, contains the ten most typical vulnerabilities like
- Damaged Object Degree Authorization,
- Damaged Consumer Authentication,
- Extreme Information Publicity,
- Lack of Sources & Charge Limiting,
- Damaged Perform Degree Authorization,
- Mass Project,
- Safety Misconfiguration,
- Injection,
- Improper Property Administration,
- Inadequate Logging & Monitoring.
An fascinating truth is that 6 out of 10 of the API vulnerabilities are similar to identified internet software vulnerabilities.
It’s value noting that
- A1. Damaged Object Degree Authorization is similar because the web-based Insecure Direct Object Reference,
- A2. Damaged Consumer Authentication with web-based Damaged Authentication and Session Administration
- A3 Extreme Information Publicity with web-based Delicate Information Publicity.
From the identified vulnerabilities from the OWASP High 10, we are able to additionally distinguish A7. Safety Misconfiguration, A8. Injection and A10. Inadequate Logging & Monitoring, as proven in my desk under.
| Yr the net app vulnerability was printed within the OWASP high 10 |
2003 |
2004 |
2007 |
2010 |
2013 |
2017 |
2021 |
| API vulnerability | |||||||
| A1. Damaged Object Degree Authorization | A4 | A4 | A4 | ||||
| A2. Damaged Consumer Authentication | A3 | A3 | A7 | A3 | A2 | A2 | |
| A3. Extreme Information Publicity | A6 | A3 | |||||
| A4. Lack of Sources & Charge Limiting | |||||||
| A5. Damaged Perform Degree Authorization | |||||||
| A6. Mass Project | |||||||
| A7. Safety Misconfiguration | A6 | A5 | A6 | A5 | |||
| A8. Injection | A6 | A6 | A2 | A1 | A1 | A1 | A3 |
| A9. Improper Property Administration | |||||||
| A10. Inadequate Logging & Monitoring | A10 |
Take a look at my earlier article on safety threats noticed by QA engineers – cybersecurity testing primarily based on our very personal TSH initiatives! It comprises a number of further information and analysis that compliments API safety – so get the massive image. I’d like to indicate you how one can simply guarantee high quality and safety consistent with the issues listed in API Safety High 10 2019 similar to I did within the final article.
In fact, all examples are primarily based on my present initiatives, so not each criterion shall be examined, and never each success present me a vulnerability ;).
Let’s start at first
“Start at first,” the King mentioned, very gravely, “and go on until you come to the tip: then cease.” – Lewis Carrol, Alice in Wonderland
Sure – let’s be methodical. I’ve put all of my examples within the order of OWASP API vulnerabilities, going from starting to finish. It will enable you discover the vulnerability that pursuits you and the way I solved the issue when working by myself initiatives.
As a reminder, right here there are so as, similar to they seem within the sections under:
- A1. Damaged Object Degree Authorization
- A2. Damaged Consumer Authentication
- A3. Extreme Information Publicity
- A4. Lack of Sources & Charge Limiting
- A5. Damaged Perform Degree Authorization
- A6. Mass Project
- A7. Safety Misconfiguration
- A8. Injection
- A9. Improper Property Administration
- A10. Inadequate Logging & Monitoring
Keep in mind that these high 10 vulnerabilities outlined by OWASP aren’t the one ones you have to be nervous about – however they’re the highest 10 most important vulnerabilities that each undertaking ought to consider. With out additional ado:
Paranoid about API vulnerabilities in your undertaking?
Information is energy – and our QA crew has the facility!
A2. Damaged Consumer Authentication

Damaged Consumer Authentication is intently associated to password administration (it permits using default or weak passwords, using ineffective password restoration processes, no password hashing, and so forth.).
It additionally permits for automated assaults akin to credential stuffing (when the attacker has a listing of legitimate usernames and passwords), brute pressure, or different computerized assaults.
An instance is a scarcity of logging out the consumer after a specified time (usually in banking functions this counter is about to 10 minutes of inactivity of the appliance).
In our functions it’s normally after 5 minutes – the net software checks whether or not the token is energetic, in any other case, the endpoint returns the worth “Unauthenticated” and logs out the consumer after an extended idle time.
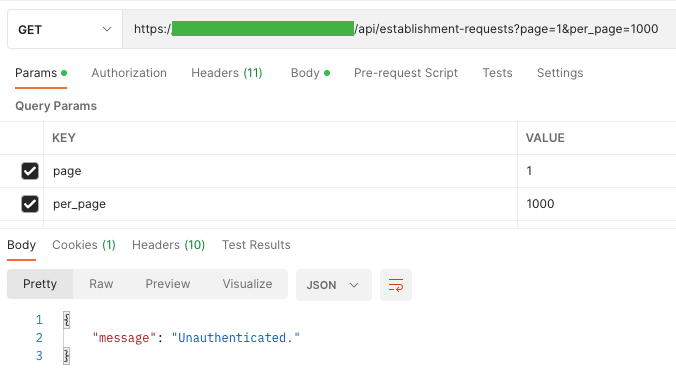
When logging in to our functions, solely what we get in response is the final 3 digits of the cellphone quantity to which the OTP code is shipped. This discovery makes me proud as a result of I can not see redundant information.
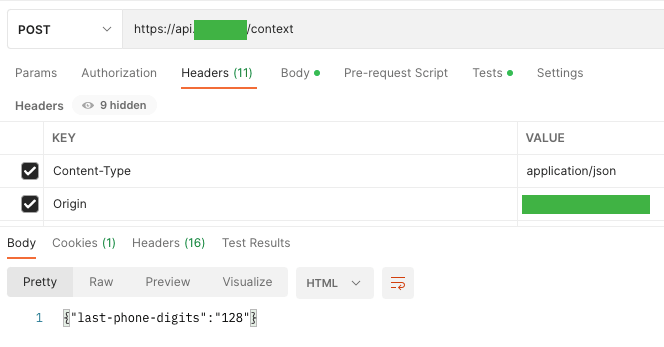
Then, after getting into the 4-digit OTP code, we’re proven a sequence of information in regards to the consumer, i.e. his account-id, user-id, e-mail, and cellphone quantity, that are vital for the authentication course of, and the cellphone quantity is 2FA (this on him comes the OTP code entered by the consumer).
As well as, the states displayed, underneath which the consumer kind is positioned. It’s value noting that the consumer’s password isn’t supplied in any of the requests, which sadly occurs in some functions.
Let’s transfer on to the following vulnerability – Extreme Information Publicity!
A3. Extreme Information Publicity

Resulting from this vulnerability, the API can return delicate information in its responses, that are filtered solely on the consumer facet.
Within the API, we are able to see a listing of information that’s not displayed on the UI facet. It’s value remembering that the responses within the API ought to comprise solely respectable information and change the overall strategies (i.e. to_string) with particular properties.
Moreover, you’ll be able to implement a response validation mechanism by which you could outline the info returned by all API strategies, together with errors.
An ideal instance is among the web sites that show only some primary details about the proprietor of the corporate on the UI facet, ie Identify, Nationwide ID, Nationality, Gender, Cellular and Electronic mail.
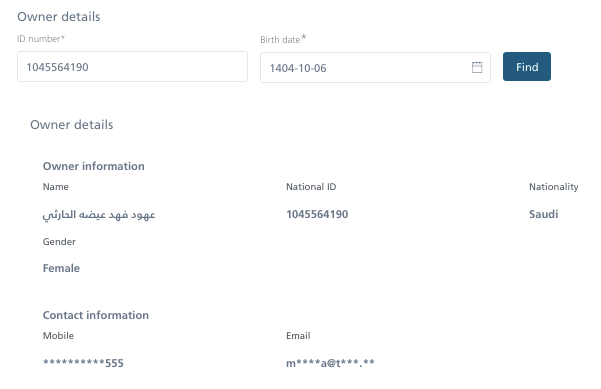
Sadly, on the API facet, we show much more info that we don’t want on the internet software facet, specifically particulars about the principle firm of this contact and his non-public handle.
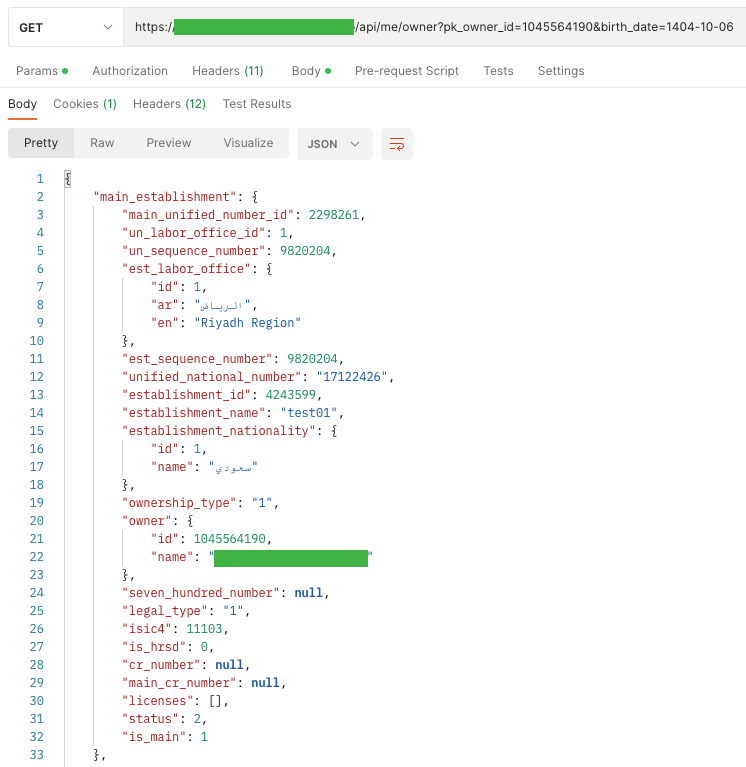
A4. Lack of Sources & Charge Limiting

The API can be susceptible to assaults when one of many following limits isn’t set: Execution timeouts, Max allocable reminiscence, Variety of file descriptors, Variety of processes, Request payload measurement, Variety of requests per consumer/useful resource, Variety of information per web page to return in a single request-response, Instance Assault Situations.
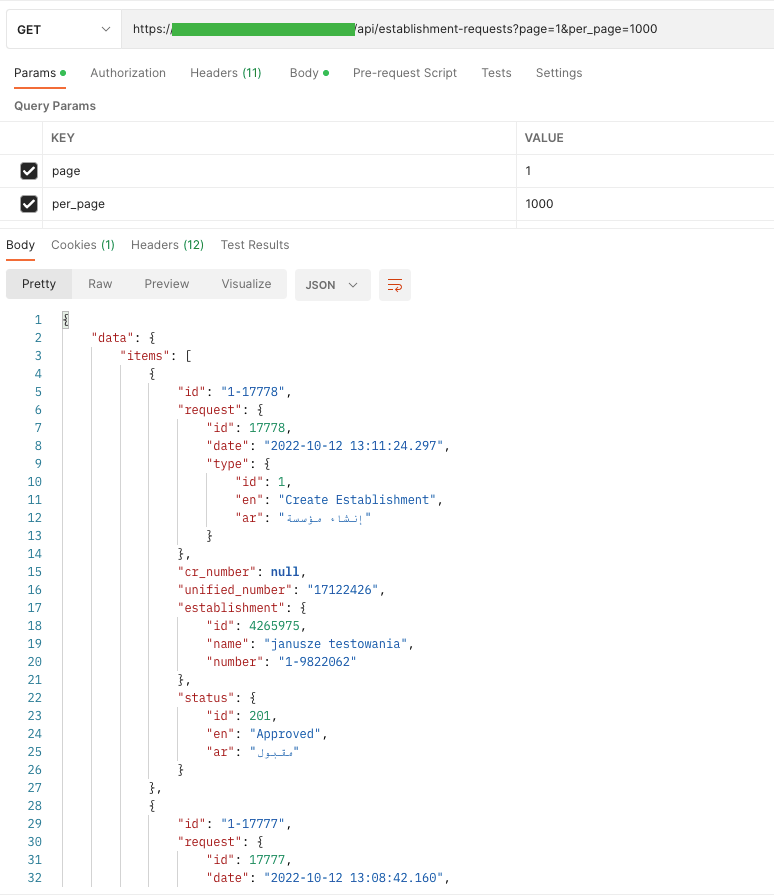
Considered one of my web sites is a consultant, the place we are able to view as much as 100 staff on the positioning. The consumer listing is retrieved from the server with the next question: / API / customers? Web page = 1 & measurement = 100. An attacker by altering the dimensions parameter to, for instance, 200,000 (if there are such a lot of or extra information), may cause database efficiency issues.
In the meantime, the API stops responding and is unable to deal with any additional requests.
On our stage, I discovered a consumer with 3409 staff.
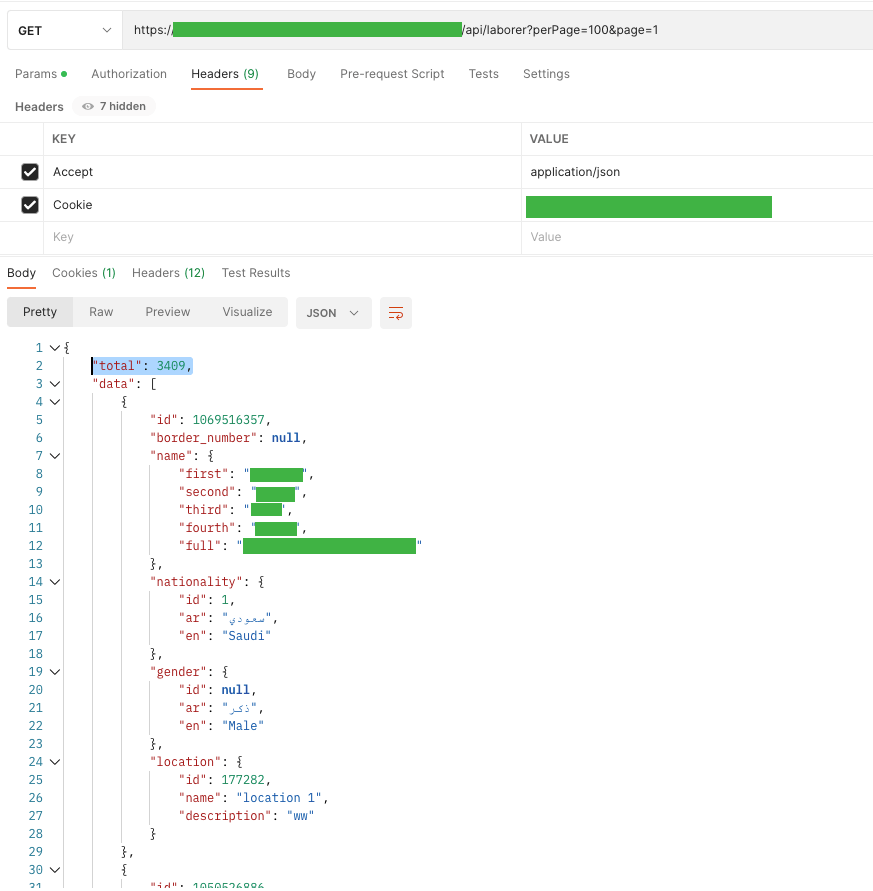
I needed to show them suddenly, however after an extended wait, I acquired a “Gateway Time-out” response by manipulating the web page perimeter.
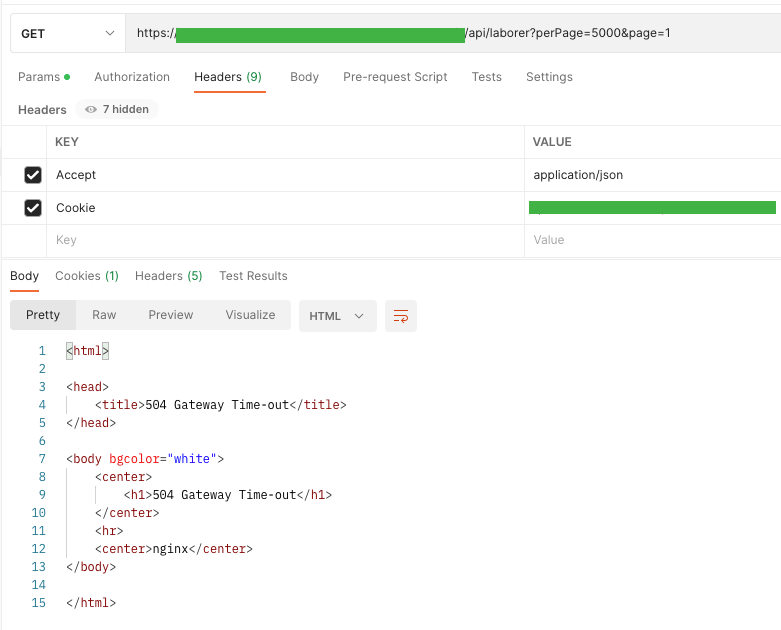
For instance the issue (when reporting a bug) I introduced this downside on the UI facet. Within the URL bar, I modified it from web page=100 to web page=4000.
As you’ll be able to see, the appliance tries to hit the identical endpoint a number of occasions. The ready time for a response to 1 question is about 1 minute, after which obtain a code with the 504 standing. The applying itself makes 4 makes an attempt.
After the final one, the consumer receives the message “One thing went unsuitable. Please strive once more later. ”. In fact, by refreshing the web page, the appliance tries to hit the endpoint 4 occasions and every time receives a timeout in response.
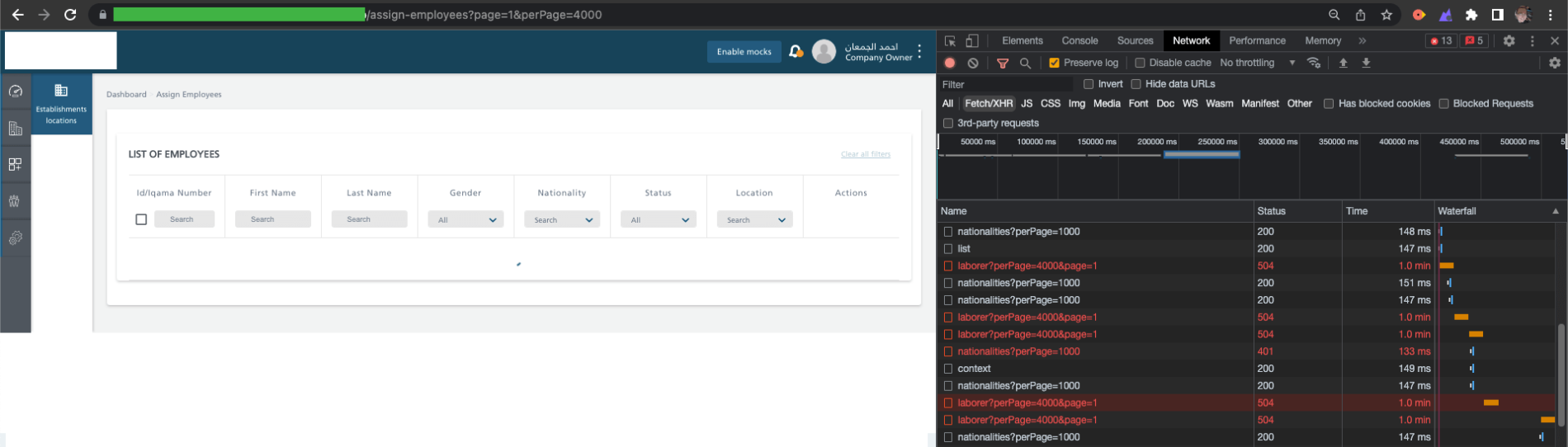
Within the occasion of an enormous assault, I dare say that the appliance will crash ;).
A6. Mass Project

Once we embody many properties in objects, and a few of them are up to date by the consumer, the endpoint API turns into susceptible if it routinely converts consumer parameters to object properties with out considering the extent of publicity and sensitivity of the property. A few of them needs to be set solely by directors, i.e. whether or not the consumer is an administrator (“is_admin”: “true”;), and process-dependent properties needs to be set solely after their prior verification.
To be on the protected facet, create a whitelist with properties that the consumer can replace and a blacklist with properties that shouldn’t be obtainable to purchasers. All schemas and endpoint inputs needs to be explicitly outlined and enforced. You also needs to keep away from features that routinely bind consumer enter into code variables or inside objects.
An instance can be file add. After efficiently including the file, it’s saved in binary format and given the UUID.
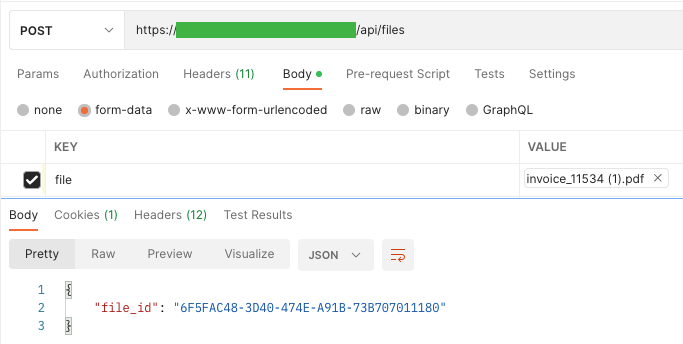
The result’s a string that’s not straight utilized by the appliance. To obtain a file, the appliance first checks the consumer’s permissions, whether or not the consumer has the request to which the file is assigned, and within the final step, permits it to be downloaded (if these assumptions are met). From the API facet, you can not obtain this file straight from one endpoint.
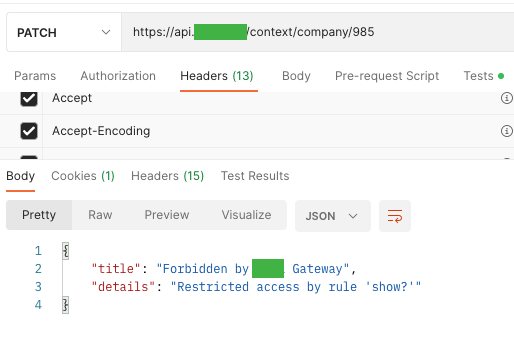
A7. Safety Misconfiguration
![]()
This vulnerability, as within the internet OWASP high 10, consists of improperly configured permissions, the dearth of the newest safety patches, safety within the transport layer (TLS), or just using outdated software program. It might even be attributable to an improperly outlined or lacking CORS (Cross-Origin Useful resource Sharing) coverage. Likewise, error messages can comprise redundant information.
It’s not doable to indicate redundant information on our web sites on the UI facet. Often, we solely show a selected error description together with its id (to make it simpler to search out the trigger within the logs). Sadly, we show redundant info on the API facet of the stage surroundings. It’s a comfort that there are not any such mishaps within the manufacturing surroundings ;).
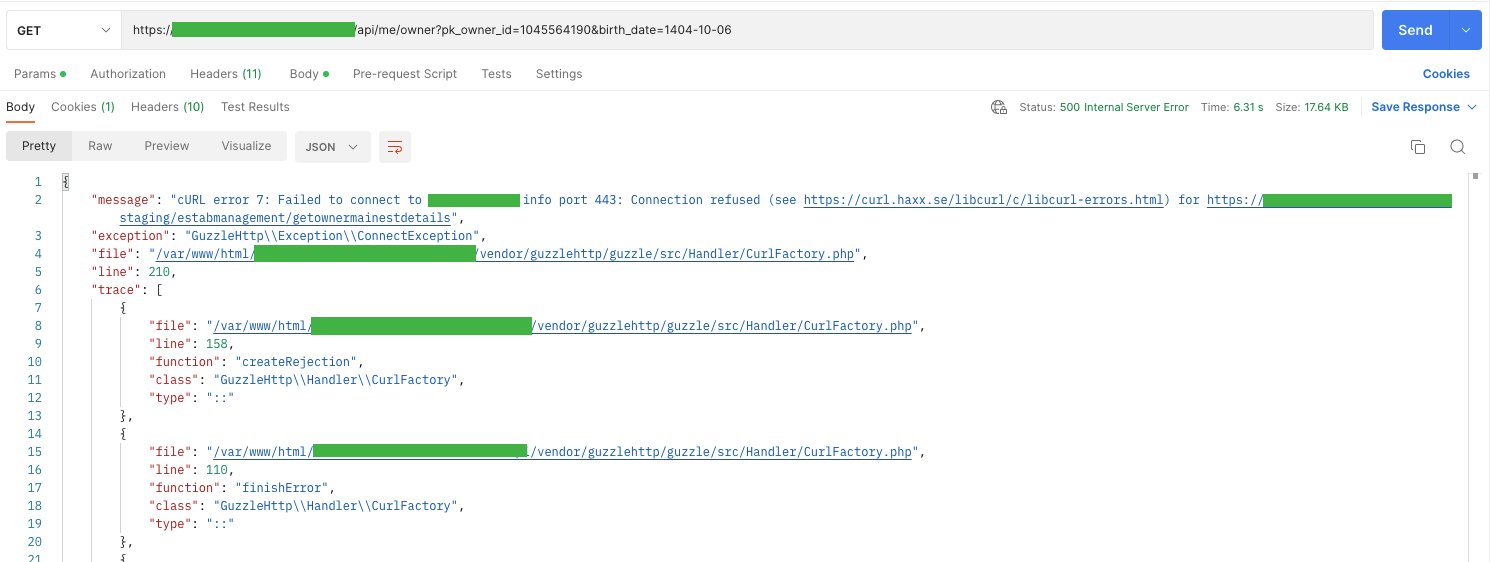
A8. Injection

The vulnerability happens when information supplied by the consumer or from exterior (built-in) programs isn’t filtered, validated, or cleaned by API in any manner, however straight used or mixed with SQL / NoSQL / LDAP queries, XML parsers, OS instructions, and so forth.
To forestall Injection, separate instructions from queries, and set up information validation utilizing a trusted and maintained library. Particular characters needs to be written descriptively (eg, “&” as “& amp;” and “<” as “& lt;”), and the variety of information needs to be restricted.
To start with, I needed to test if there are Cross-Web site Scripting (XSS) assaults, which, based on the newest internet OWASP High 10, have been mixed into one vulnerability with Injection. As within the earlier article, Mirrored XSS went first. Out of curiosity, I attempted to parse a URL request from:
/api/laborer?perPage=100&web page=1
to:
/api/laborer?perPage=<script>alert(XSS)</script>
To show a pop-up window with the textual content “XSS” (this is among the flagship methods to detect this vulnerability).
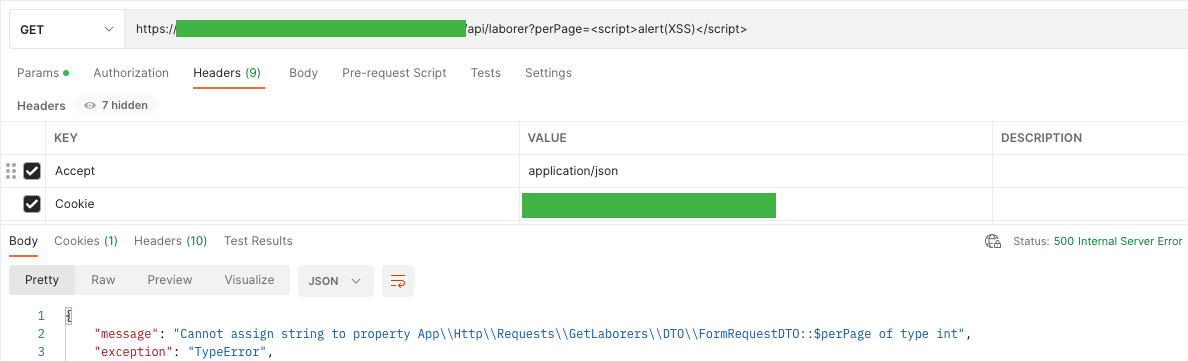
API answered me with code 500 – Inner Server Error and displayed details about the unsuitable information kind
“Can not assign string to property App Http Requests GetLaborers DTO FormRequestDTO :: $ perPage of kind int”
Equally, I needed to check if there’s Saved (Persistent) XSS, i.e. saving the XSS code as one of many parameters within the database.
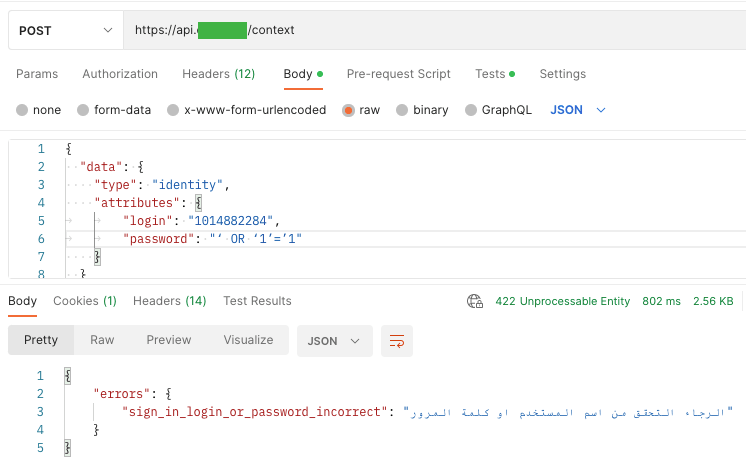
Within the screenshot above you’ll be able to see that the placement has been added accurately. Thankfully, API safety treats XSS code as a string and doesn’t load it.
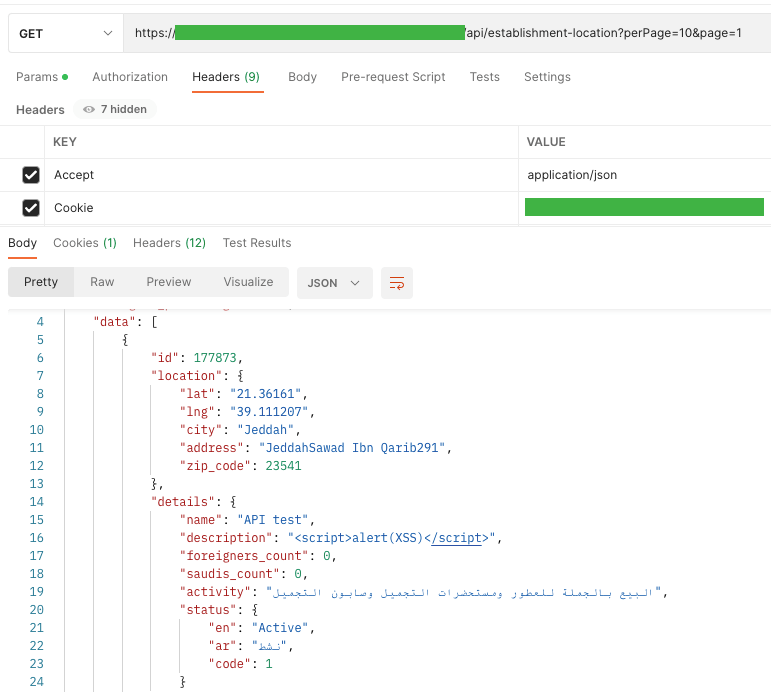
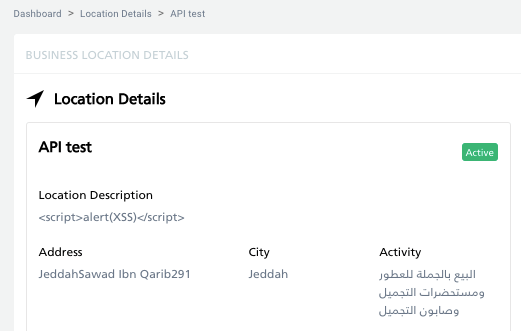
To point out that XSS positively doesn’t seem within the internet software, I did it in parallel. The situation has appeared within the listing of places and no alert has been displayed. Within the location particulars, within the description area, you’ll be able to discover an added, damaged script.
Injection vulnerability isn’t solely XSSy, however most of all SQL injection, PHP Injection, and so forth. And as in nearly each tutorial, to test SQL Injection vulnerability, I needed to analyze whether or not the consumer could fail to offer a password or login utilizing SQL code, which is at all times true or is the start of a remark:

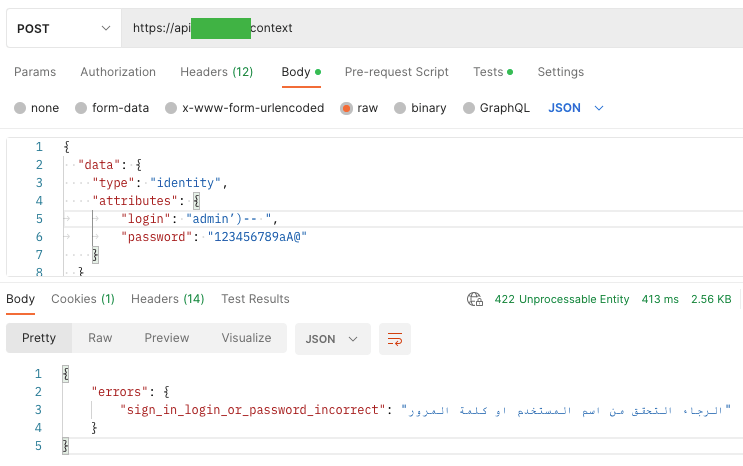
In each circumstances, I acquired the reply “sign-in login or password incorrect” with the code 422 – Unprocessable Entity.
It’s identified that the above examples should not determinants of whether or not the vulnerability of SQL Injection happens, however are solely meant to indicate the method. It’s value attempting, opening as much as assessments, and attempting once more (altering parameters or names). As I discussed within the earlier article, the admin identify doesn’t need to be admin however can encompass a string of numbers, and so forth.
A9. Improper Property Administration

This vulnerability happens when the documentation isn’t up to date or lacking. When there isn’t any built-in companies stock, host stock, and so forth., or they’re outdated.
When there isn’t any clear info on what surroundings the API is operating on (stage, UAT, growth, prod, and so forth.), who ought to have entry to it and which model is operating? Failure to replace such info or its full absence has nice penalties. For instance, the attacker, figuring out the vulnerability of the older API model, could attempt to reproduce this bug on the newer model.
To forestall this from taking place, create documentation that shall be frequently up to date. It ought to comprise a listing of all hosts, details about environments, accesses, and API variations. And above all, it’s value remembering that API documentation needs to be made obtainable solely to these licensed to make use of the API.
The documentation on our web sites is comparatively up-to-date. It’s on this foundation that frontend builders write an online software, and our backend is a hyperlink and extra safety between the net software and the API.
A10. Inadequate Logging & Monitoring

The vulnerability happens when no logs are generated or their integrity isn’t ensured. And when the API infrastructure and logs should not always monitored.
This vulnerability doesn’t happen in our functions, as we now have a number of completely different instruments to gather details about what is occurring within the functions. In fact, we don’t retailer delicate and even redundant information. In every device, we now have customized dashboards, due to which we combination info and are capable of shortly point out the place and when the issue started.
It might be a great observe to combine a device akin to Airbrake (gathering errors generated by functions and aggregating outcomes) with Slack or different communicators utilized by everybody at work, the place everybody may have details about the incident regularly.
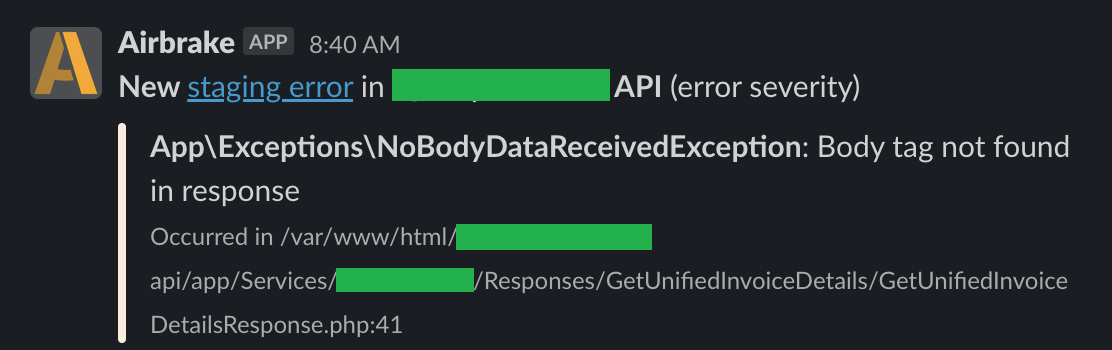
Be ready!
In conclusion, testing the API for safety isn’t as tough because it might sound, and it’s extraordinarily necessary.
There are conditions when safety issues are solely patched on the consumer facet, and utilizing the API alone, we’re capable of recreate them. By exposing the API, we expose a variety of different functions / IoT that use it. Due to this fact, we should always begin with guaranteeing API safety to repair any imperfections on the facet of the ultimate functions. It needs to be remembered that software safety isn’t solely safety on the consumer’s facet.
I hope that the article will encourage somebody to at the very least attempt to determine a number of vulnerabilities, to search out out that safety testing isn’t so scary and tough, and above all, to make sure the safety of the appliance. And I hope it conjures up companies to create safer, much less susceptible apps – you want some vulnerability in your life, however nowhere close to the place the enterprise of constructing functions is anxious.
Impressed with our information?