QA specialists are on the frontlines of cybersecurity. We now have the chance to work in several branches of software program tasks, like community safety, net, and cell purposes, API – you title it. In every single place QA engineers discover themselves, they’ve a chance to enhance their tasks and determine safety threats. On this article, I’m going to indicate you my strategy to a mission with cybersecurity testing necessities – and the way I handled them technically with the assistance of OWASP.
Should you’re a QA doing vulnerability assessments and are coping with delicate information tasks, I hope to indicate you one thing new that can make it easier to together with your mission. This is a crucial facet of QA work – as a result of high quality is about safety, and QAs who’re capable of talk with each builders and purchasers are in quickly rising demand.
I see that issues are altering and builders are reporting a necessity for good QA engineers. Not simply people who find themselves going to “click-through” a mission and examine for small errors or do computerized safety testing, however be lively contributors in product design and growth.
QA – the newly appreciated cybersecurity testing warriors
As a QA engineer at The Software program Home, I’ve had the chance to work with an enormous international company that implements options for his or her authorities. Authorities web sites, it doesn’t matter what nation they’re in, deal with an unimaginable quantity of delicate info and private information – this made me assume much more about end-user safety.
And we’re not solely speaking concerning the US, Canada, or EU laws containing provisions on the safety of the move and processing of non-public information just like the Normal Knowledge Safety Regulation (GDPR), which is the harshest legislation on this planet proper now.
Misplaced in translation – the first step in safety is attending to know the shopper
When working with worldwide purchasers, you need to take into consideration each the authorized elements and work tradition of elements of the world just like the Center East, Africa, Australia, or in our case, West Asia.
As I discovered, it’s best to positively begin by getting conversant in your finish shopper’s work surroundings and situations. What might sound irrelevant to us and is one thing that we are able to’t foresee as a result of we don’t even give it some thought would possibly truly be a delicate information leak hiding in plain sight.
For instance, after speaking to the Product Proprietor and having a chat, I realized that a number of individuals in several positions and with completely different safety entry could use the identical pc station.
This illustrates why a proactive strategy needs to be taken by the QA to get to know all the information – each onerous and smooth. That’s important with a view to discover out about all of the threats that the entire group would possibly miss in any other case.
What are you able to study from OWASP?
My information about threats to net purposes relies primarily on the rankings of the worldwide non-profit basis OWASP (The Open Internet Software Safety Mission®).
OWASP is a non-profit neighborhood based in 2001. They produce instruments, documentation, analysis, articles, and methodologies that every one must do with net software safety. In addition they set up conferences and workshops on trade requirements. OWASP tasks are supported by the OWASP Basis. Should you’re not conversant in their work, you’re behind!
OWASP’s analysis, carried out on the idea of danger evaluation lately, allowed for the presentation and specification of strategies. These had been the event of instruments, and remedial actions in reference to guaranteeing the safety of IT methods. Additionally, the operation of enterprises implementing web purposes to enhance enterprise processes.
Conducting case research, the OWASP group has been creating rankings of the most typical net software threats since 2003, referred to as OWASP High 10. The primary one was created in 2003 and, like every subsequent one, it contained the ten most typical threats.
Updates ensuing from the altering habits of net software customers, in addition to the development of safety breach instruments, occurred in 2004, 2007, 2010, 2013, 2017, and 2021.
It’s price analyzing the dynamics and developments of the final twenty years. It’s simple to note that new threats have been added, however the positions of these beforehand listed have additionally modified in subsequent rankings. Beneath is a desk I made containing all vulnerabilities from stories ready over 18 years and the positions assigned to them within the rating (from A1 – the most typical to A10 – the least frequent).
| Identify | 2003 | 2004 | 2007 | 2010 | 2013 | 2017 | 2021 |
| Invalid Parameters / Inputs | A1 | A1 | |||||
| Damaged Entry Management | A2 | A2 | A5 | A1 | |||
| Damaged Authenticathion and Session Administration | A3 | A3 | A7 | A3 | A2 | A2 | |
| Cross Web site Scripting <XSS, CSS> | A4 | A4 | A1 | A2 | A3 | A7 | |
| Buffer Overflow | A5 | A5 | |||||
| Injection | A6 | A6 | A2 | A1 | A1 | A1 | A3 |
| Error Dealing with Issues | A7 | ||||||
| Insecure Use of Cryptography | A8 | ||||||
| Distant Administration Flaws | A9 | ||||||
| Internet and Software Server Misconfiguration | A10 | ||||||
| Improper Error Dealing with | A7 | ||||||
| Insecure Storage | A8 | ||||||
| Software Denial of Service | A9 | ||||||
| Insecure Configuration Administration | A10 | ||||||
| Malicious File Execution | A3 | ||||||
| Insecure Direct Object Reference | A4 | A4 | A4 | ||||
| Cross Web site Request Forgery <CSRF, XSRF> | A5 | A5 | A8 | ||||
| Info Leakage and Improper Error Dealing with | A6 | ||||||
| Insecure Cryptographic Storage | A8 | ||||||
| Insecure Communications | A9 | A9 | |||||
| Failure to Prohibit URL Entry | A10 | A8 | |||||
| Safety Misconfiguration | A6 | A5 | A6 | A5 | |||
| Insecure Direct Object References | A7 | ||||||
| Unvalidated Redirects and Forwards | A10 | A10 | |||||
| Delicate Knowledge Publicity | A6 | A3 | |||||
| Lacking Operate Degree Entry Management | A7 | ||||||
| Utilizing Parts with Recognized Vulnerabilities | A8 | A9 | |||||
| XML Exterior Entities | A4 | ||||||
| Insecure Deserialization | A8 | ||||||
| Inadequate Logging & Monitoring | A10 | ||||||
| Cryptographic Failures | A2 | ||||||
| Insecure Design | A4 | ||||||
| Weak and Outdated Parts | A6 | ||||||
| Identification and Authentication Failures | A7 | ||||||
| Software program and Knowledge Integrity Failures | A8 | ||||||
| Safety Logging and Monitoring Failures | A9 | ||||||
| Server-Aspect Request Forgery SSRF | A10 |
Personal examine based mostly on A. Sołtysik-Piorunkiewicz, M. Krysiak, “The Cyber Threats Evaluation for Internet Purposes Safety in Trade 4.0, Springer 10.1007 / 978-3-030-40417-8_8, 2020, p. 134
It’s also price taking note of the 7 most ceaselessly recurring net software threats (occurring 3 or extra instances).
You’ll discover that Injections are listed in every of the rankings. The following ones on the checklist are
- Damaged Authentication,
- Session Administration,
- and Cross-Web site Scripting (XSS, CSS),
which seem in stories from 2003-2017.
Different widespread threats are Safety Misconfiguration (famous between 2010-2021) and Damaged Entry Management (which had been famous in 2003 and 2004 to be returned in 2017 and 2021 stories), and Insecure Direct Object Reference and Cross-Web site Request Forgery (CSRF, XSRF), as proven within the determine under.
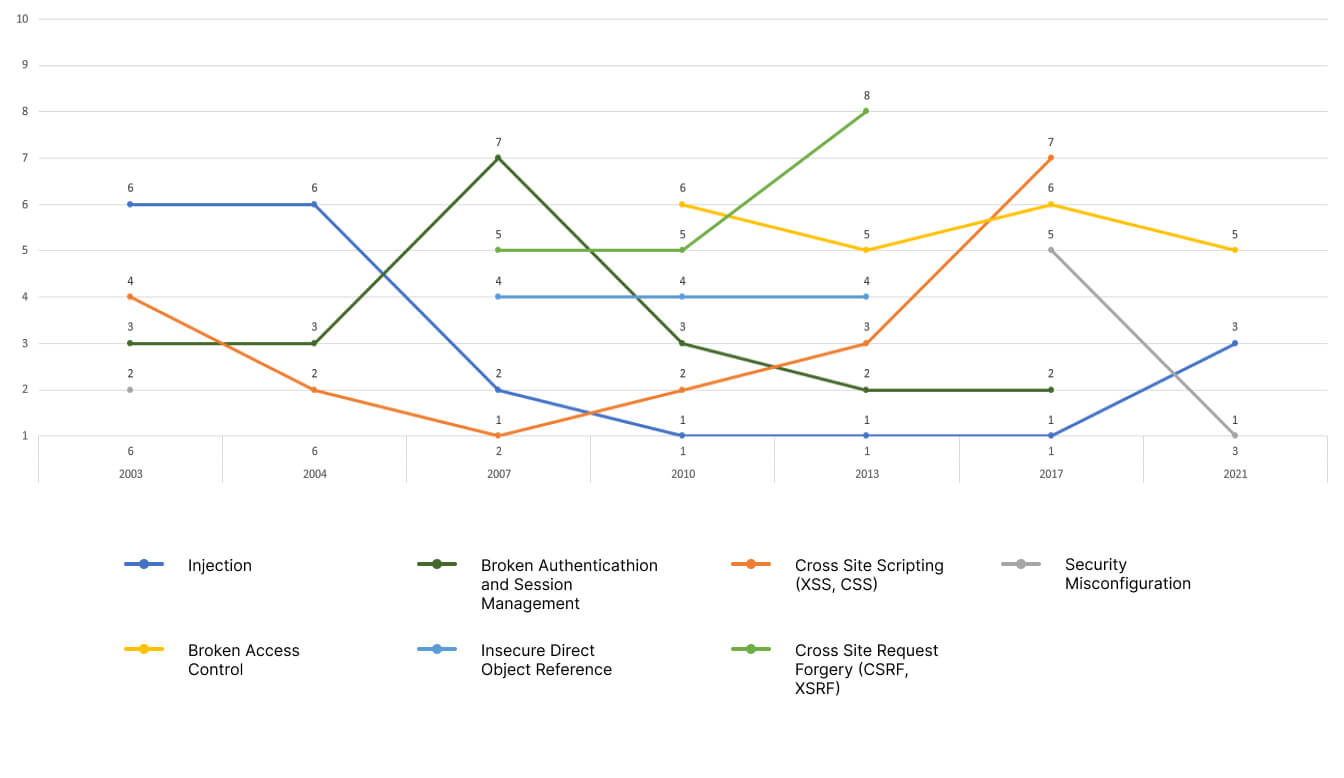
Personal analysis, A. Sołtysik-Piorunkieicz, M. Krysiak, “Modern threats to Web software safety within the gentle of OWASP analysis”, Wydawnictwo Politechniki Częstochowskiej, 2022, p. 267
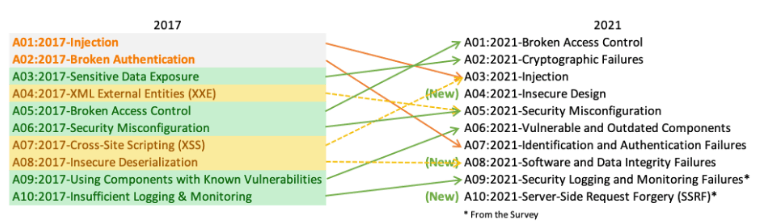
Along with my colleague Adam Gola we attempt to create an evaluation of modifications to grasp the most recent developments and threats, each time the OWASP High 10 rankings are up to date.
After all, I like to recommend his article: on the High 10 Vulnerabilities on the variations within the newest stories (2017 and 2021). It’s price commenting on the shortage of compliance within the title of the report.
Adam used 2020 within the title as a result of the primary model of OWASP High 10 was launched on the finish of 2020, however the closing model was accessible in early 2021. Try The OWASP 2021 examine. An image of the most recent modifications is on the display screen under.
The 2022 OWASP High 10 report received’t be accessible till late 2022 or early in 2023.
However sufficient of concept! Let’s see some actual work and easily present how to make sure high quality based mostly on a few of the issues talked about within the OWASP High 10 2021.
After all, all of the examples are based mostly on my present mission, subsequently not all standards will probably be examined and described. One standards is a A10 Server Aspect Request Forgery (SSRF), which might be simply examined. You want a element that could be a area to which the person is to offer the URL to an exterior useful resource, in order that the appliance will obtain and show the output.
Simply attempt to enter the handle resulting in a file on the native disk, utilizing e.g. file: /// and so forth / passwd, which clearly signifies that the appliance lets you obtain any recordsdata from the disk.
For this reason on this article I centered on:
- A1 Damaged Entry Contol,
- A3 Injection,
- A4 Insecure Design,
- A7 Identification and
- Authentication Failures, and
- A9 Safety Logging and Monitoring Failures.
1. OWASP High 10: 2021 A1 Damaged Entry Contol
Following the “OWASP High 10: 2021” rating, Damaged Entry Contol is the most typical risk.
This vulnerability permits for unauthorized entry to information, e.g. by manipulating parameters within the URL handle. For instance, having a request with id = 10, the person will change the worth from 10 to 11 within the URL handle and the appliance information with the quantity id = 11.
This makes any person capable of entry your info. It is a pretty easy factor to identify, and intensely essential from a safety perspective. Many individuals are knowledgable sufficient that as an alternative of clicking on the hyperlink in an software, they substitute ID values in URLs and, by inadvertent (and generally even deliberate) motion, could acquire unauthorized entry to information.
A really comparable case is logging from person A’s account after which logging into person B’s account. I occurred to be on the tab with my firm particulars, logged out, and logged into one other person to carry out one other check.
At this level, it turned out that the URL just isn’t cleared after logging out and the brand new person was capable of see person A’s firm information.
The preliminary repair was to load the web page with clean fields (all values had been changed with “-“), however in my view, it isn’t the very best methodology as person B noticed person A’s firm quantity within the URL. One other repair was cleansing the URL in order that the subsequent person wouldn’t have the ability to see any information from the earlier person. Because of this, every logged-in person instantly after logging in goes to the service’s Dashboard.
I had the same scenario after I switched from a person with larger privileges to a person with decrease privileges.
A person with larger privileges may view all purposes (submitted by different customers) and edit them. I previewed the X software and logged right into a low-privilege person. It turned out that I may see the main points of X’s request.
I appeared on the checklist of requests submitted by this person and it turned out that he had by no means submitted one. That is one other unacceptable scenario the place a given person has an opportunity to see one other person’s delicate information (with out even interfering with the URL).
And identical to within the earlier situation, for unauthorized customers, the builders first modified the values into “-“, and solely within the subsequent patch they cleaned your entire URL handle in order that it was not even attainable to suspect the appliance quantity.
This case is essential as a result of the shopper confirmed that there are firms in which there’s just one pc and it’s utilized by completely different workers (with completely different ranges of authorization).
2. OWASP High 10: 2021 A3 Injection
Third on the OWASP High 10 checklist is Injection. It’s a class centered on numerous sorts of injections, equivalent to SQL injection, PHP Injection, and so forth.
Since final 12 months, it has been mixed with the Cross-Web site Scripting (XSS) class, which was distinctive till 2017.
Cross-Web site Scripting (XSS) assaults by themselves might be divided into three classes:
- Mirrored XSS,
- Saved <Persistant> XSS,
- and DOM-based XSS.
I’m going to concentrate on the primary two for testing. Every of them might be examined in a reasonably easy manner:
- Mirrored XSS – happens when a part of the HTTP request is mirrored within the output (e.g. when sending a hyperlink). Out of curiosity, I attempted to parse a URL request from:
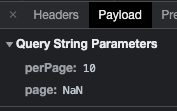
https://establishment-location-management-api.qiwa.information/api/laborer?perPage=100&web page=1to:https://establishment-location-management-api.qiwa.information/api/laborer?perPage=<script>alert(XSS)</script>
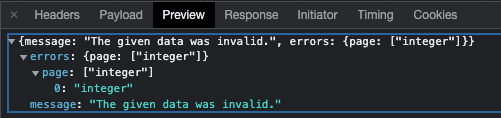
- To show a pop-up window with the textual content “XSS” (this is without doubt one of the flagship methods to detect this vulnerability). After all, the safety on the web site mechanically modified the request to:
https://establishment-location-management-api.qiwa.information/api/laborer?perPage=10&web page=NaN
Checking in DevTools, the GET methodology acquired the standing 422 – Unprocessable entity, because it anticipated to obtain an integer worth, not a string. The web page then reloaded the proper information.

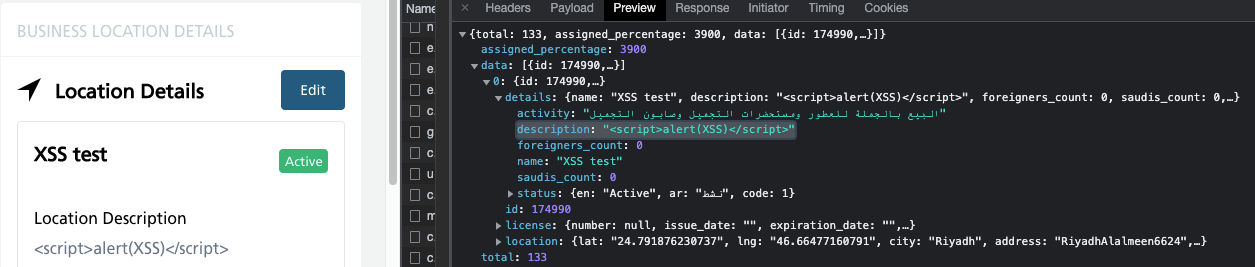
- Saved (Persistent) XSS – happens when the XSS code is saved within the database, e.g. as a weblog remark. Equally to the primary case, I wished to make use of the <script> alert (XSS) </script> phrase when including an outline to the shape I’m filling out.
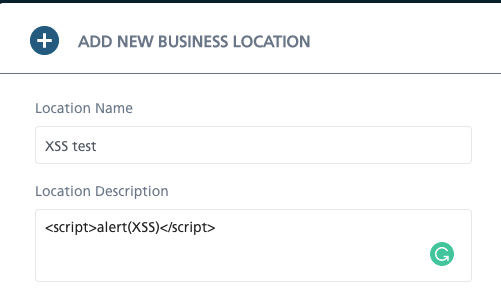 This manner, I realized that the React framework makes certain that characters are encoded, and the appliance doesn’t ship requests containing “malicious” code, however solely reads it as a remark.
This manner, I realized that the React framework makes certain that characters are encoded, and the appliance doesn’t ship requests containing “malicious” code, however solely reads it as a remark.
- It’s equally essential to examine if there is no such thing as a chance of injections throughout logging (eg SQL Injection). This vulnerability could result in unauthorized entry to the database, ensuing within the studying of knowledge, i.e. logins and passwords, bypassing the authentication mechanism, code execution, and so forth.
- Flagship examples are variations on the easy SQL question language code:
- utilizing the next code within the password area: ‘OR’ 1 ‘=’ 1, which theoretically lets you log into the system and not using a password, because the situation (1 = 1) is at all times met.
- utilizing the code within the login area: admin ‘) – which theoretically lets you log in because the admin person, as a result of “-” is the start of the remark, so the password is not going to be checked within the database.
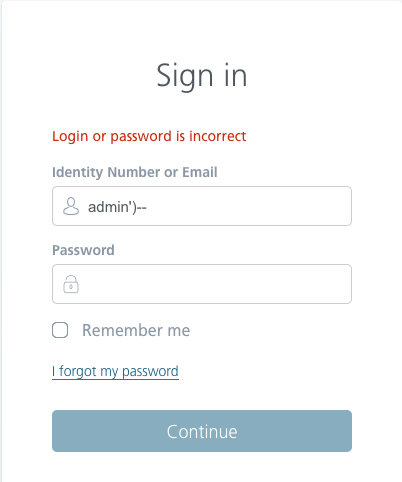
After all, that’s not the case after the primary try and with precisely such a fraction of the code, we will discover an SQLi vulnerability.
To start with, the administrator’s title doesn’t must be admin, however administrator, or it should be a collection of numbers or a very completely different title. It’s price attempting completely different variations, and the examples proven above are supposed to current the method in order that it will be comprehensible even for an individual who doesn’t write SQL scripts.
To start with, the administrator’s title doesn’t must be admin, however administrator, or it should be a collection of numbers or a very completely different title. It’s price attempting completely different variations, and the examples proven above are supposed to current the method in order that it will be comprehensible even for an individual who doesn’t write SQL scripts.
3. OWASP High 10:2021 A4 Insecure Design
The A4 Insecure Design class is the debut of the present report. It’s a broad class that focuses on the dangers related to the design and architectural flaws. It’s speculated to make you conscious of attainable dangers within the mission on the design stage and doesn’t confer with the implementation itself.
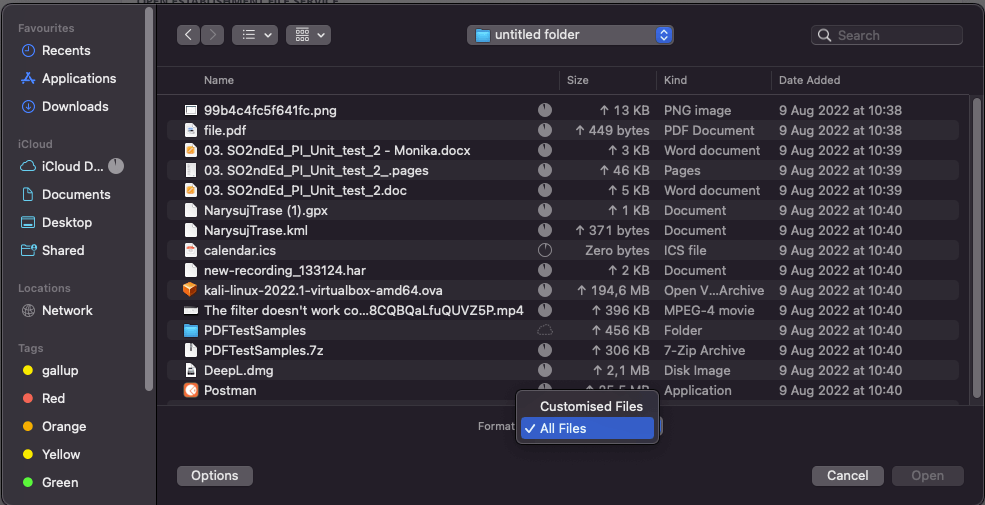
An instance could be the file add perform. Crucial factor is to examine that solely recordsdata with the allowed extension can truly be added. For instance, when choosing recordsdata, the person ought to solely have the ability to choose these with a particular extension (on this case .png, .jpeg, .jpg, and .pdf), the remaining shouldn’t be attainable so as to add.
After all, the person can manually change the file explorer to permit including any file extension (simply within the format choice, set the worth to “All Information”).
A superb follow is that regardless of including a forbidden file, it doesn’t save anyplace (in our mission on the UI facet, it appears as if the person didn’t choose any file). Because of this, it isn’t attainable to add a malicious .exe file, and so forth.
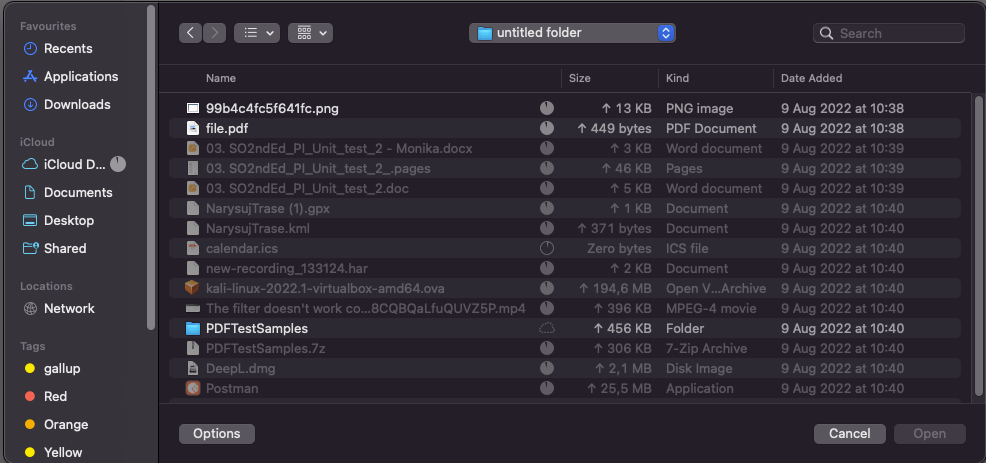
After all, it occurs {that a} file, though it has a very good extension (e.g. .png), is definitely an .exe file. Such information might be procured by opening the file, e.g. in a pocket book, and altering it to a forbidden extension.
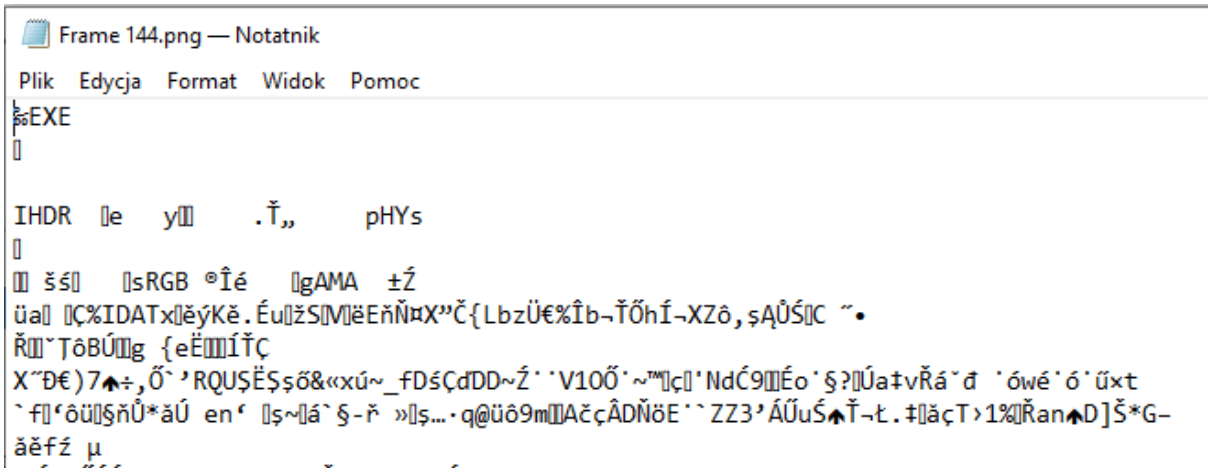
That is what an try at opening the file in Paint appears like:
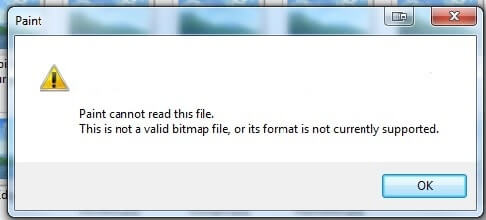
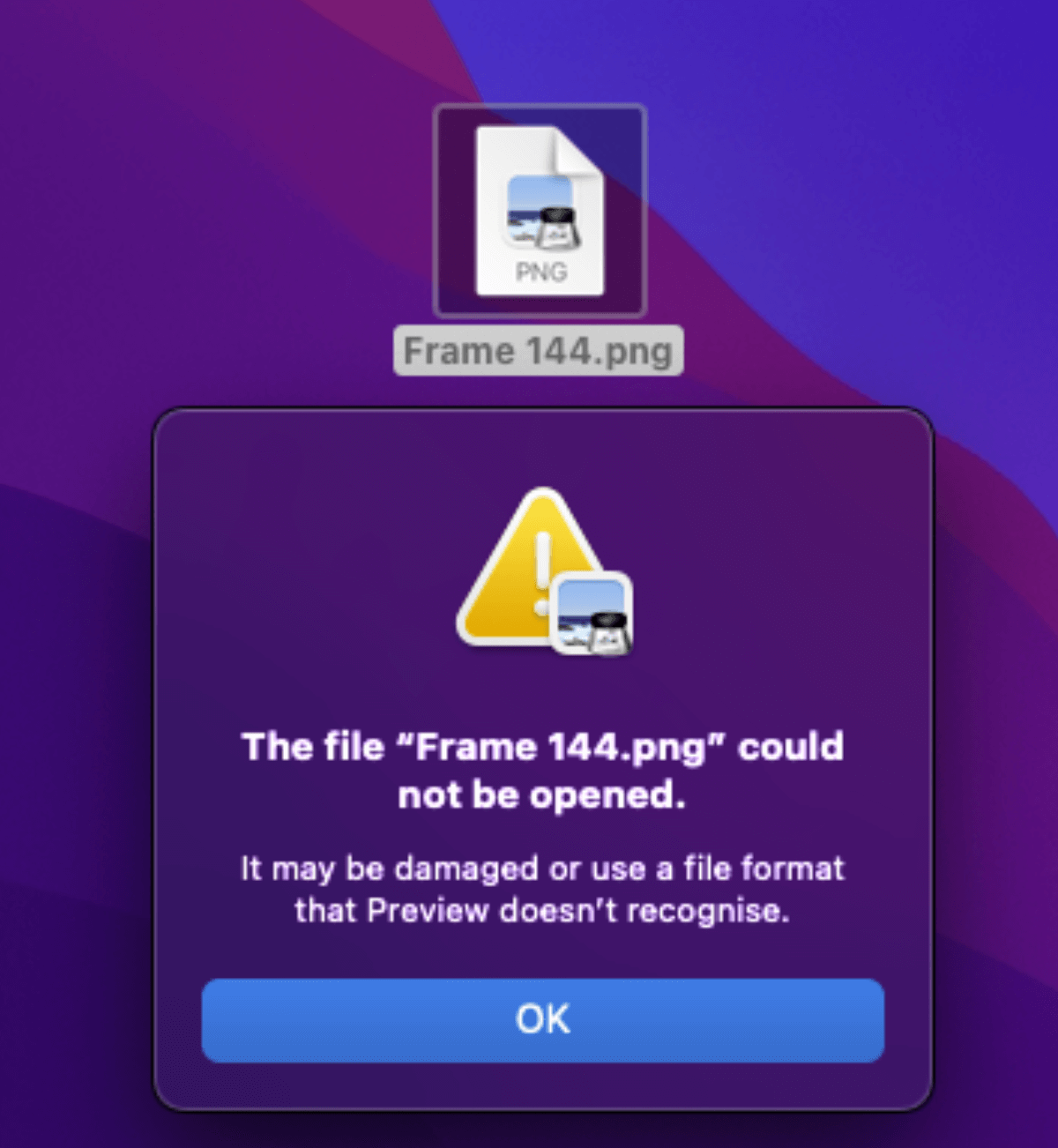
On macOS, at first look, the file’s icon doesn’t increase any doubts, however after attempting to open it, we are going to get the data that it might be a broken or unseen file.
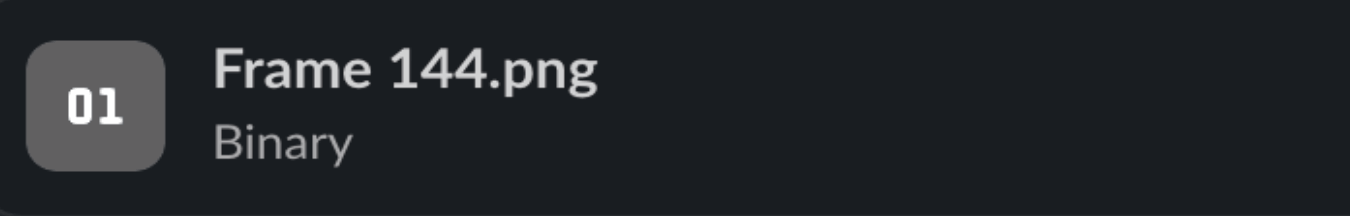
Apparently, Slack instantly acknowledges that it isn’t a picture and signifies that it’s a binary.
After attempting to add such a file, our software shows a message about an unlawful extension, and the file itself just isn’t saved anyplace.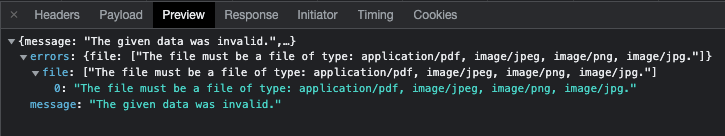
4. OWASP High 10:2021 A7 Identification and Authentication Failures
One other vulnerability is A7 Identification and Authentication Failures, in regards to the login and error dealing with elements of the appliance.
It’s recognized that logging in to your software is a key aspect of many flows, so we are able to simply confirm {that a} CAPTCHA is not going to seem after getting into an incorrect login or password a number of instances. It is a nice safety methodology from a buyer’s perspective, but it surely’s not excellent both.
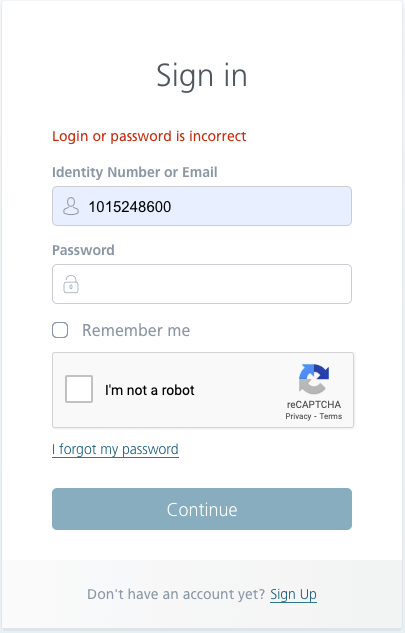
After all, a greater methodology of securing in opposition to a brute drive assault is to implement throttling, which limits the frequency of accepted connections. Checking it manually, sadly, just isn’t an choice, as a result of sending, for instance, 2 requests in 1 second is not possible to carry out. You possibly can attempt to do it by sending requests from the API, however on this article, I centered on the elements of handbook testing.
As well as, it will be important that after getting into a unsuitable password, the person doesn’t obtain a message that they entered it incorrectly, as a result of, for an unauthorized particular person, it is going to be a transparent sign that such a person already exists within the database. The attacker will now have the ability to concentrate on this explicit login.
The identical goes for restoring passwords. A greater message is to point that the password or login is inaccurate, thus the attacker just isn’t certain of any of the values.
When restoring the password, it’s price checking whether or not the person has been logged out of all classes (as a failure to take action could trigger an unauthorized particular person related to one of many classes to make the same transfer and substitute the password with one other one). Extra safety could also be a message that an e-mail with a password change has been despatched. If such an e-mail handle doesn’t exist within the database, the reset e-mail won’t ever be despatched.
One other downside with resetting passwords and creating accounts is imposing on the person the situations that the password should meet, i.e.
- higher case letters,
- decrease case letters,
- numbers, and
- particular characters.
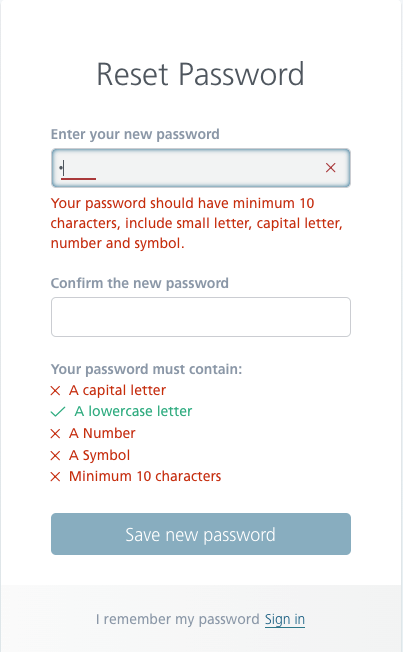
This commonplace is presently being deserted. After all, the person ought to have a password longer than 1 character (a minimal of 12 and a most of 127 characters is an effective follow). Current analysis reveals that utilizing a passphrase, not essentially with particular characters, is far safer than utilizing one or two phrases with a number of particular characters and numbers (eg Adm! N1). It’s also a very good follow to permit for using areas, emoticons, and diacritics in a password. Consultants additionally extremely advocate using password managers.
5. OWASP High 10: 2021 A9 Safety Logging and Monitoring Failures
The final one I’ve for you is A9 Safety Logging and Monitoring Failures, which considerations information saved in logs and error dealing with.
I truthfully admit that this risk just isn’t verifiable by each QA. This isn’t as a result of a scarcity of our expertise, however as a result of a scarcity of entry to logs. In my present mission, virtually every of us has the chance to see logs, so it’s price taking note of what information is saved there. Generally the appliance doesn’t log delicate information outlined in accordance with native laws or privateness coverage, delicate information, together with session IDs, passwords, hash strings, or API tokens.
And above all, whether or not the appliance returns error messages that include delicate information can assist attackers. This consists of session IDs, software program/platform variations, and private info. Within the case of error messages from our purposes, there is no such thing as a query of exhibiting redundant information. We attempt to deal with all errors in every of the web sites in the same manner.
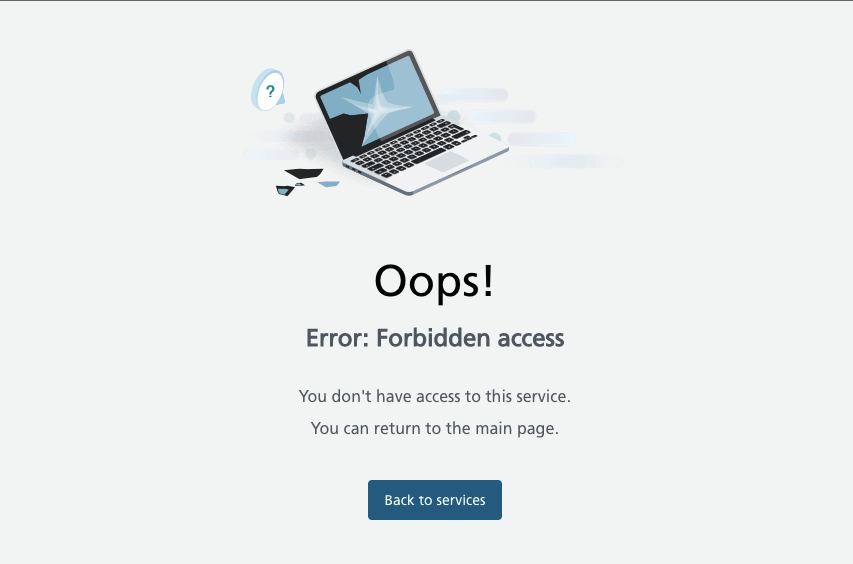
After all, we aren’t saints; not each case has been predicted and designed a lot upfront. Every time we attempt to preserve the usual to indicate the person as little technical particulars as attainable, as within the image under.
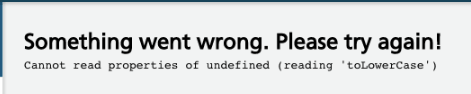
It’s also price remembering that when displaying an error, when “one thing goes unsuitable”, the person has the choice to return to the earlier step or reload the web page.
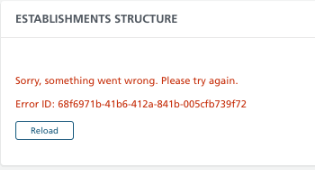
It isn’t strictly associated to security, however to good practices and guaranteeing the standard of our product!
Do not forget that we QA should not solely chargeable for the looks and clicking by the assessments. It’s rather more severe than that. High quality assurance must be essential to us, not solely by seamlessly crossing the road to UX and efficiency but additionally by net safety elements.
There are completely different requirements on the Web, relying on the shopper’s location. I attempt to concentrate on the outcomes of the OWASP group and their OWASP High 10 Internet Software Safety Dangers stories on net purposes. It’s essential that you simply too keep knowledgeable concerning the modifications. Contemplate watching any upcoming OWASP international occasions – get into it!
It’s price mentioning that in 2016 a report was developed:
OWASP Cell High 10, which might be discovered right here:
https://owasp.org/www-project-mobile-top-10/
And 2019 for API safety:
OWASP API Safety Mission, which might be discovered right here:
https://owasp.org/www-project-api-security/
The group itself has many instruments, not just for pentesters, but additionally for QAs, builders, and designers to create probably the most safe purposes attainable. I hope that with this text, I inspired you to concentrate to safety of their mission, and my examples will show to be precious suggestions!
Deal with your mission from each security angle!
We love our QA, and we hope you’ll too!